The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
Search Results For - Command Line
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
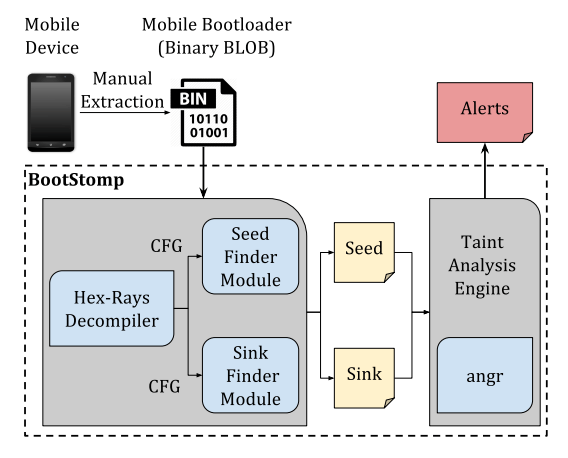
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
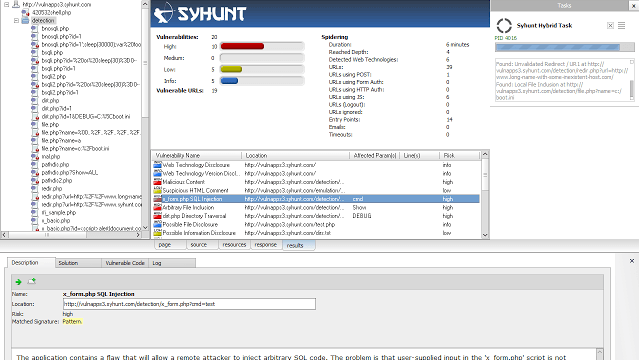
Syhunt ScanTools 6.0 adds advanced fingerprinting capabilities, enhanced spidering, injection and code scan capabilities, and a large number of improved checks...
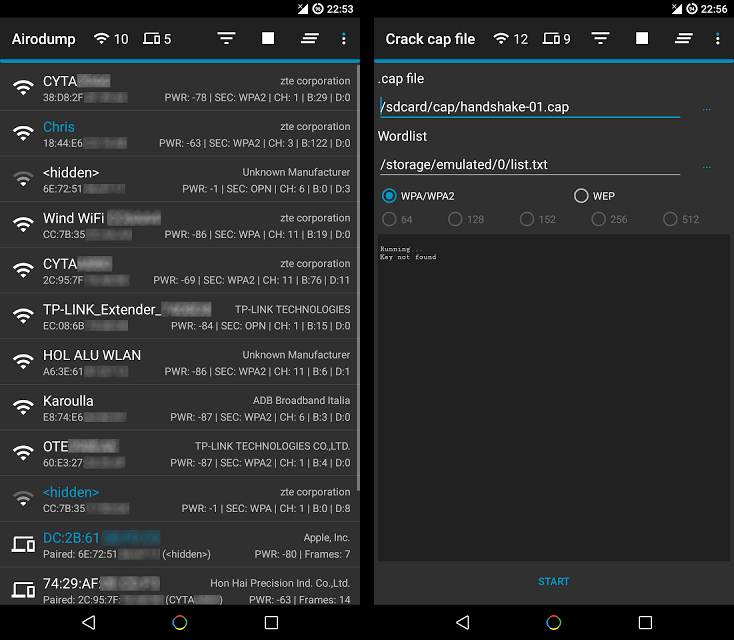
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
DR.CHECKER: A Soundy Vulnerability Detection Tool for Linux Kernel Drivers Tested on Ubuntu >= 14.04.5 LTS 1. Setup The implementation is based on LLVM...
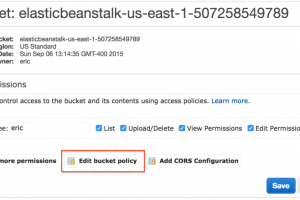
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...