[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
Search Results For - Code Analysis
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] Based on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in web applications, Web...
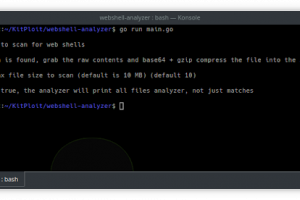
[sc name=”ad_1″] Web shell analyzer is a cross platform stand-alone binary built solely for the purpose of identifying, decoding, and tagging files...
[sc name=”ad_1″] Manuka is an Open-source intelligence (OSINT) honeypot that monitors reconnaissance attempts by threat actors and generates...
[sc name=”ad_1″] “”” What is this register used for? Hmm.. I’ll just rename it to veryuniquename, do a textual search, and...
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a...
[sc name=”ad_1″] Polypyus learns to locate functions in raw binaries by extracting known functions from similar binaries. Thus, it is a firmware...
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...