[sc name=”ad_1″] Cheetah Mobile—a prominent Chinese app company, known for its popular utility apps like Clean Master and Battery Doctor—and one of...
Search Results For - Client Side
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
Cryptocurrencies such as Bitcoin have been gaining more and more public attention over recent years. Now, the digital currency industry has hit Hollywood with...
GlobaLeaks is open-source / free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
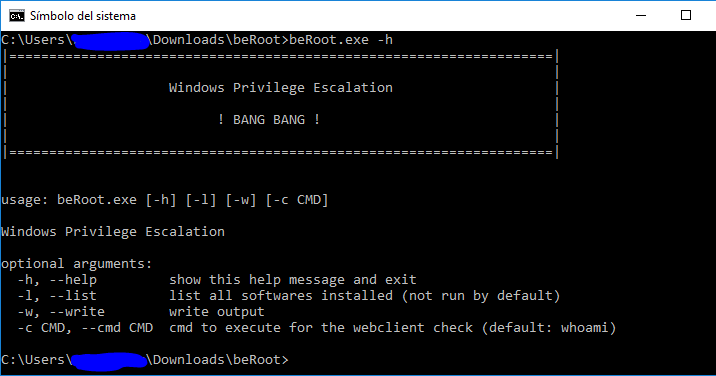
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...