[sc name=”ad_1″] Utility to find AES keys in running process memory. Works for 128, 192 and 256-bit keys. Usage Open aes-finder.sln solution in...
Search Results For - C2
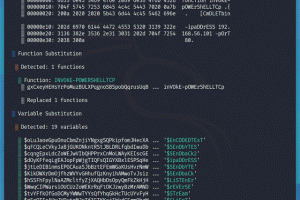
[sc name=”ad_1″] Chimera is a (shiny and very hack-ish) PowerShell obfuscation script designed to bypass AMSI and antivirus solutions. It digests...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
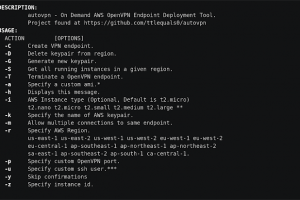
[sc name=”ad_1″] Script that allows the easy creation of OpenVPN endpoints in any AWS region. To create a VPN endpoint is done with a single...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
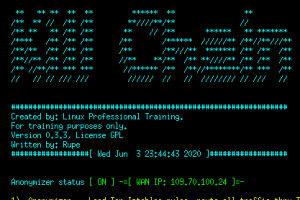
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing page and phishing hunting...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] ezEmu enables users to test adversary behaviors via various execution techniques. Sort of like an “offensive framework for...