The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
Search Results For - C2
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as...
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
CrunchRAT currently supports the following features: File upload File download Command execution It is currently single-threaded (only one task at a time), but...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
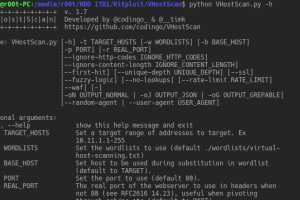
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
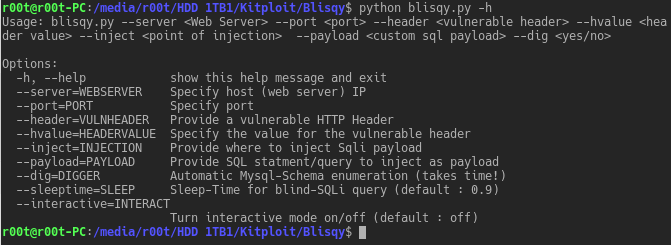
A slow data siphon for MySQL/MariaDB using bitwise operation on printable ASCII characters, via a blind-SQL injection. Usage USAGE: blisqy.py --server <Web...
Habu is to teach (and learn) some concepts about Python and Network Hacking. These are basic functions that help with some tasks for Ethical Hacking and...