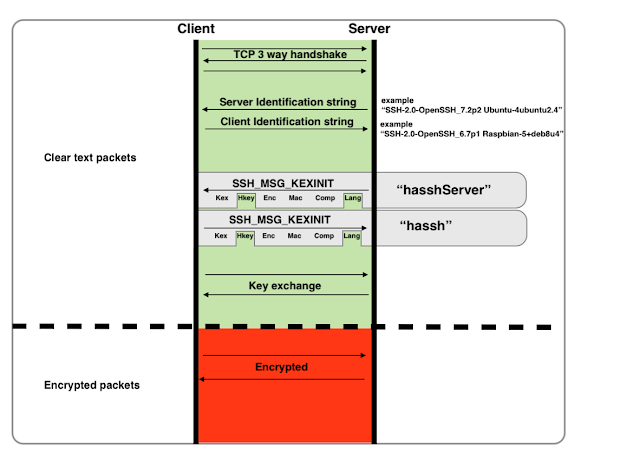
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
Search Results For - Brute Force
In an effort to secure users’ data while maintaining privacy, Google has announced a new security measure for Android Backup Service that now encrypts...
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
Sn1per Community Edition is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Sn1per...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
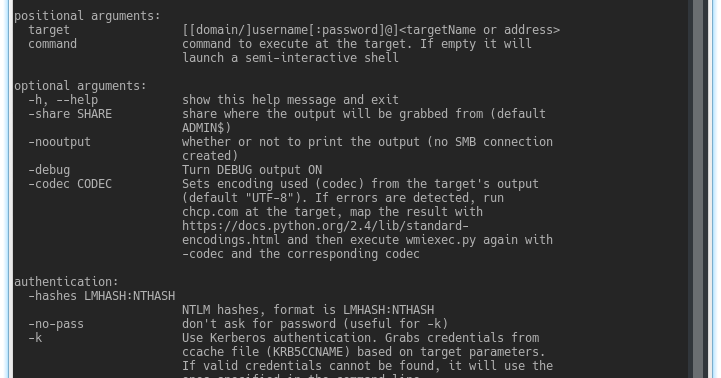
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
Sn1per is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Features: Automatically collects basic...
theHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources...
Tool to check if a given IP is a node tor or an open proxy. Why? Sometimes all your throttles are not enough to stop brute force attacks or any kind of massive...
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...