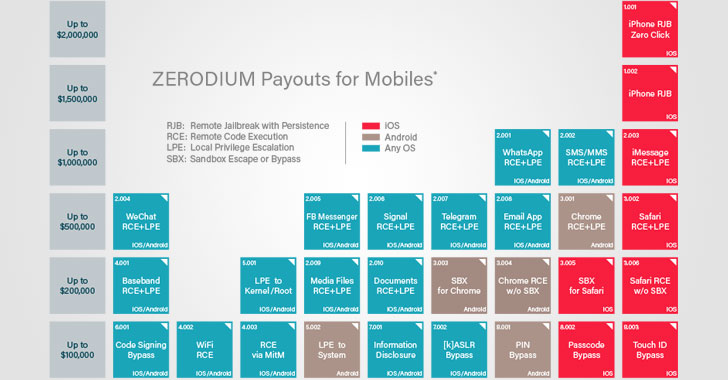
[sc name=”ad_1″] Well, there’s some good news for hackers and vulnerability hunters, though terrible news for tech manufacturers! Exploit...
Search Results For - Browsers
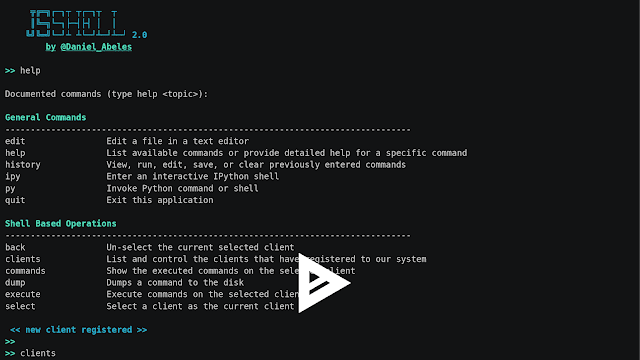
[sc name=”ad_1″] An interactive multi-user web based javascript shell. It was initially created in order to debug remote esoteric browsers during...
[sc name=”ad_1″] Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions...
[sc name=”ad_1″] Microsoft today, on its year-end December Patch Tuesday, released security updates to patch a total 39 vulnerabilities its Windows...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
[sc name=”ad_1″] It is no secret how miserably Microsoft’s 3-year-old Edge web browser has failed to compete against Google Chrome despite...
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
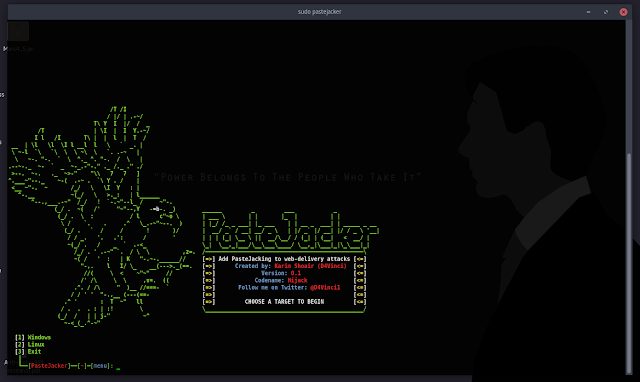
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
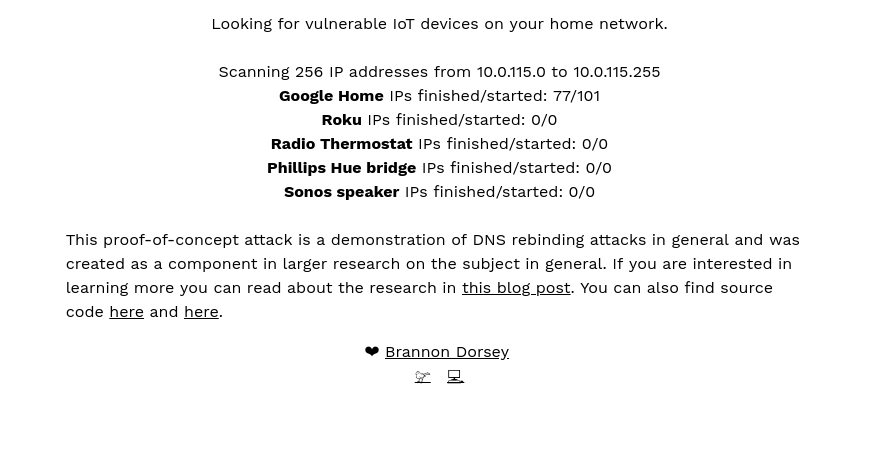
DNS Rebind Toolkit is a frontend JavaScript framework for developing DNS Rebinding exploits against vulnerable hosts and services on a local area...