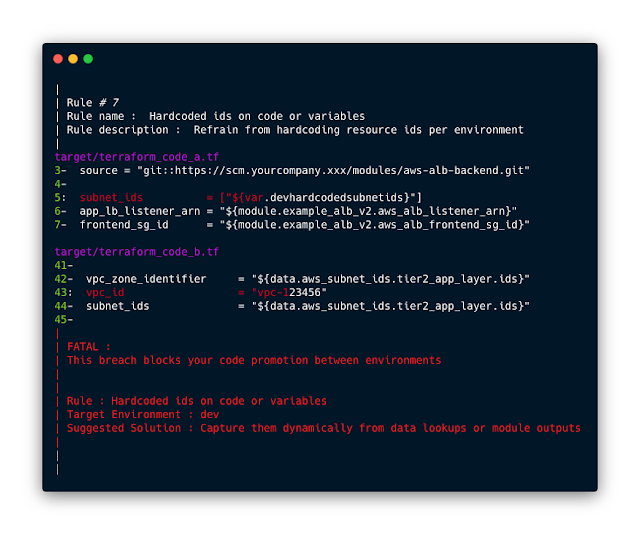
[sc name=”ad_1″] Stupidly easy to use, small footprint Policy as Code subsecond command-line scanner that leverages the power of the fastest multi...
Search Results For - Binary
[sc name=”ad_1″] Integration of Clair and Docker Registry (supports both Clair API v1 and v3) Klar is a simple tool to analyze images stored in a...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
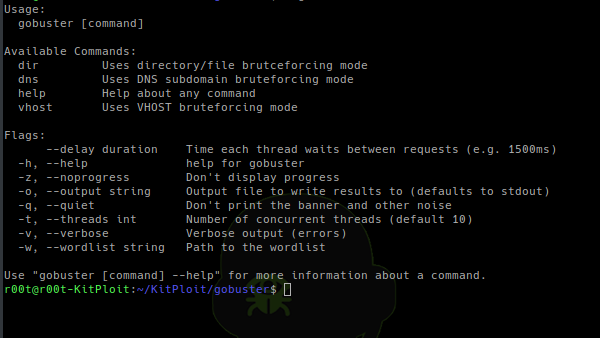
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual...
[sc name=”ad_1″] uniFuzzer is a fuzzing tool for closed-source binaries based on Unicorn and LibFuzzer. Currently it supports fuzzing 32-bits LSB...
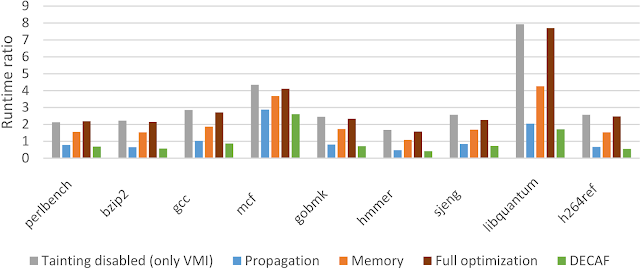
[sc name=”ad_1″] DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole...
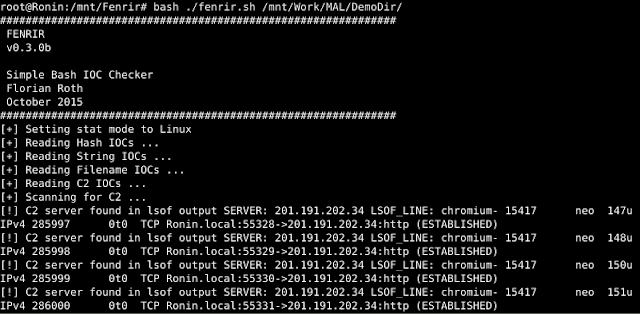
[sc name=”ad_1″] Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise...
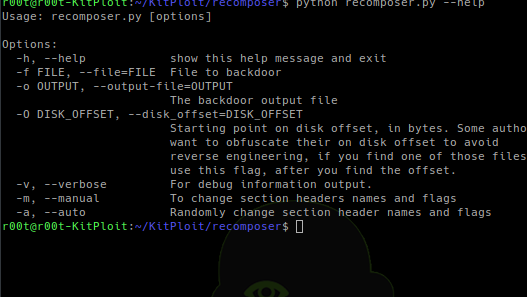
[sc name=”ad_1″] Ever have that not so safe feeling uploading your malware binaries to VirusTotal or other AV sites because you can look up...
[sc name=”ad_1″] flare-emu marries IDA Pro’s binary analysis capabilities with Unicorn’s emulation framework to provide the user with an easy to...
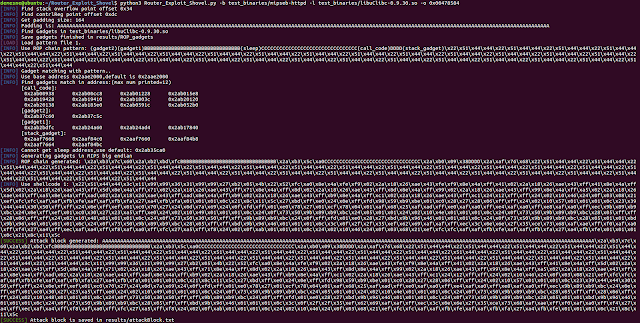
[sc name=”ad_1″] Automated Application Generation for Stack Overflow Types on Wireless Routers. Router exploits shovel is an automated application...