sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
Search Results For - BIND
The firm looked at nearly 70 million emails sent during October from 5,000 different .gov origin domains preserved by Proofpoint, the company’s VP of Email...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
Mail header analyzer is a tool written in flask for parsing email headers and converting them to a human readable format and it also can: Identify hop delays...
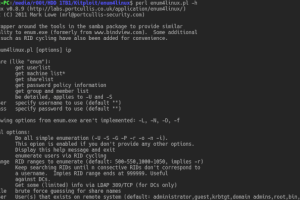
A Linux alternative to enum.exe for enumerating data from Windows and Samba hosts. Enum4linux is a tool for enumerating information from Windows and Samba...
A wrapper tool for shadowsocks to consistently bypass firewalls. Quick start Automatically connect The easiest way to run this tool is just type ssct in...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
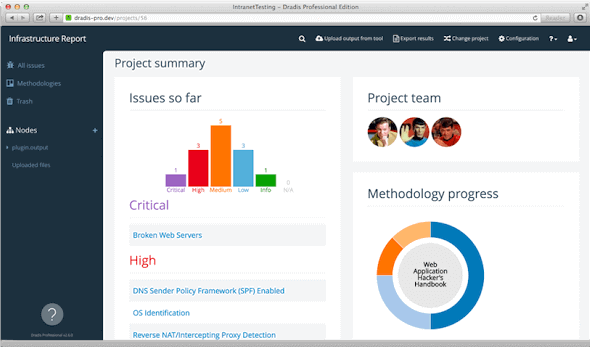
Dradis is an open-source collaboration framework, tailored to InfoSec teams. Goals Share the information effectively. Easy to use, easy to be adopted...
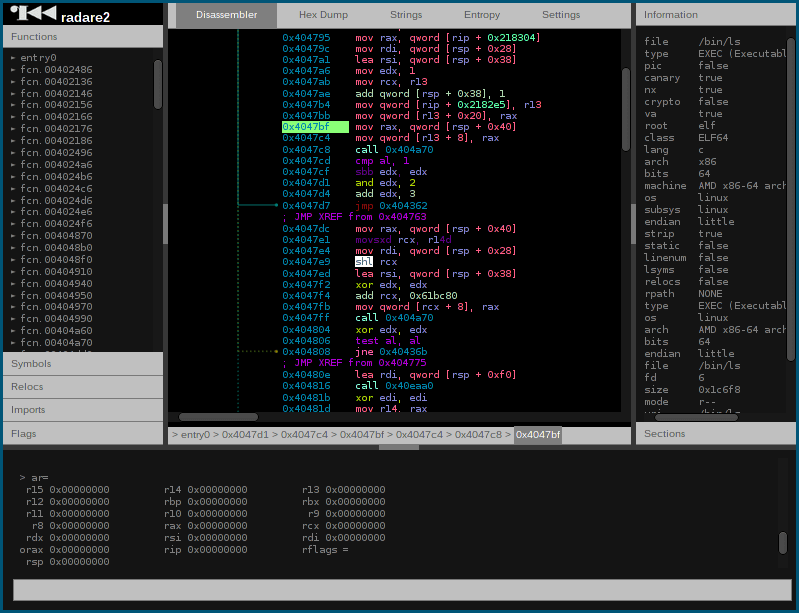
r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. The radare project started as a forensics...