v3n0m is a free and open source scanner. Evolved from baltazar’s scanner, it has adapted several new features that improve functionality and usability. It is...
Search Results For - Arch Linux
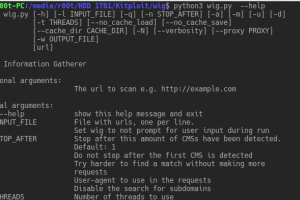
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
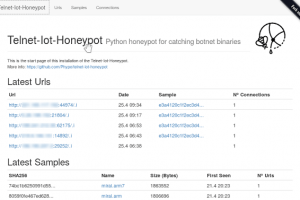
This project implements a python telnet server trying to act as a honeypot for IoT Malware which spreads over horribly insecure default passwords on telnet...
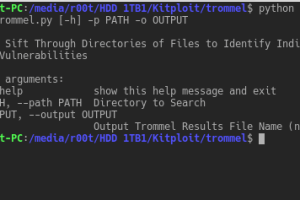
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
FireEye’s Innovation and Custom Engineering (ICE) team released a tool called GoCrack that allows red teams to efficiently manage password cracking tasks...
Exploit Pack has been designed by an experienced team of software developers and exploit writers to automate processes so penetration testers can focus on...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...