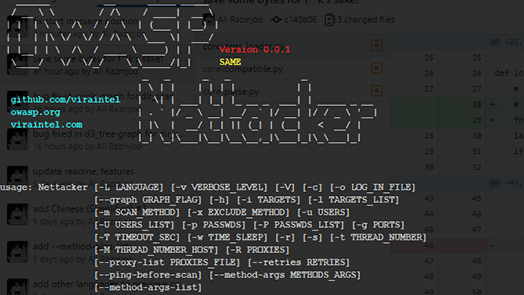
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Search Results For - Analysis
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
State-of-the-art password guessing tools, such as HashCat and John the Ripper (JTR), enable users to check billions of passwords per second against password...
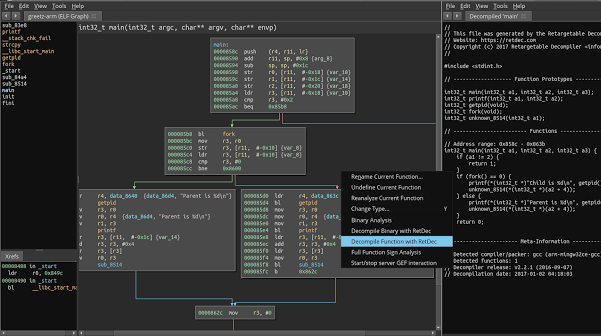
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
Chiron is an IPv6 Security Assessment Framework, written in Python and employing Scapy. It is comprised of the following modules: • IPv6 Scanner • IPv6 Local...
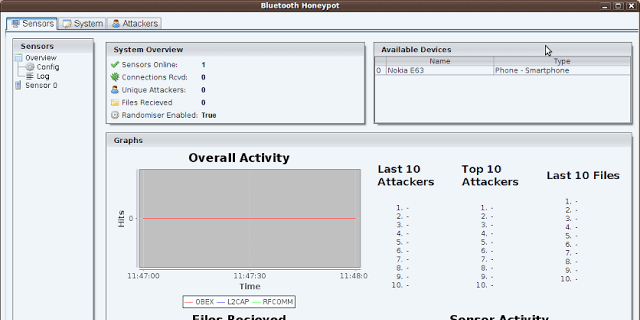
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in...
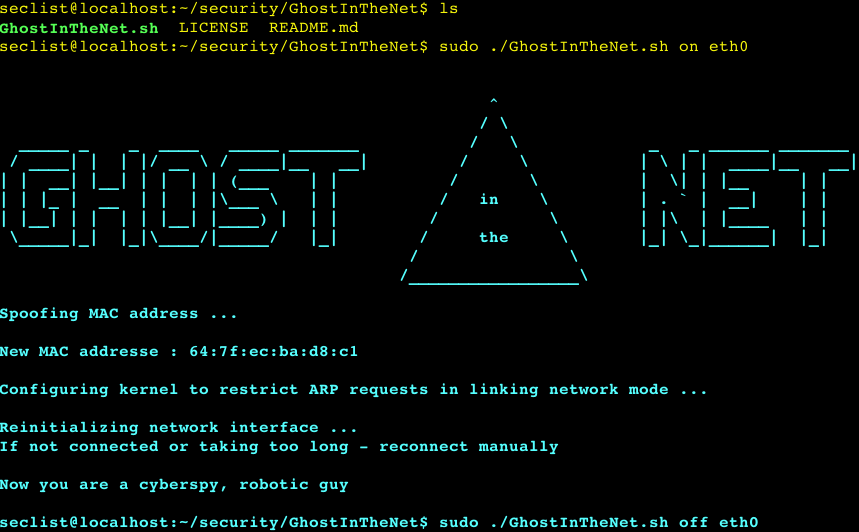
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...