[sc name=”ad_1″] What is cross-site scripting (XSS)? Cross-site scripting (also known as XSS) is a web security vulnerability that allows an...
Search Results For - Analysis
[sc name=”ad_1″] BSF provides a discrete simulation environment to implement and extend peer-to-peer botnets, tweak their settings and allow...
[sc name=”ad_1″] Espionage is a network packet sniffer that intercepts large amounts of data being passed through an interface. The tool allows...
[sc name=”ad_1″] Spyse is a cybersecurity search engine for finding technical information about different internet entities, business data, and...
[sc name=”ad_1″] Sherlock, a powerful command line tool provided by Sherlock Project, can be used to find usernames across many social networks. It...
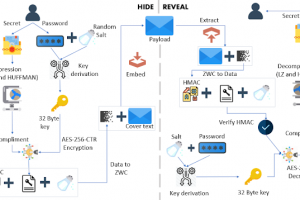
[sc name=”ad_1″] StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside text by...
[sc name=”ad_1″] In this malware, are used some techniques to try bypass the AVs, VMs, and Sandboxes, with only porpuse to learning more. I’m...
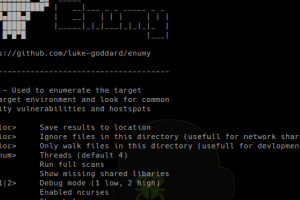
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] This new release brings strong improvements to your security team’s daily performance, allowing them to operate quicker and...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...