The streaming company retweeted its care for the Internet Association’s Friday announced it would “interrupt in a judicial action to save net neutrality...
Search Results For - Amazon
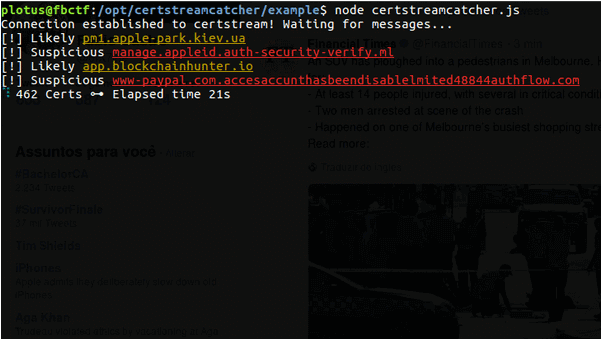
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
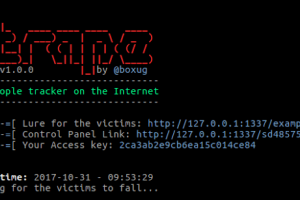
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
The macro_pack is a tool used to automatize obfuscation and generation of MS Office documents for pentest, demo, and social engineering assessments. The goal...
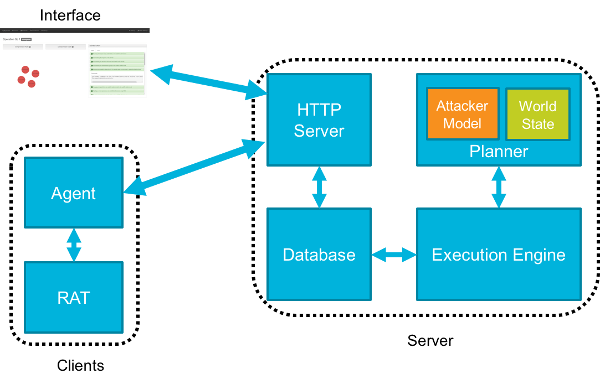
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
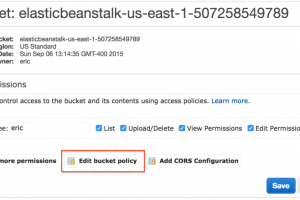
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
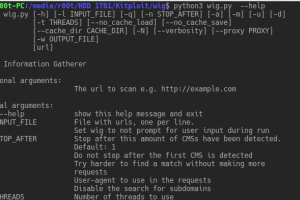
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
As we’ve seen, that’s been shifting. With a new game from companies like Hulu and Amazon, Netflix has seen running deals get pricier and customers get antsier...