[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
Search Results For - Active Directory
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] Sinter is a 100% user-mode endpoint security agent for macOS 10.15 and above, written in Swift. Sinter uses the user-mode...
[sc name=”ad_1″] Terminal and Web console for Kubernetes Features Configuration from kubeconfig files (KUBECONFIG environment variable or $HOME/...
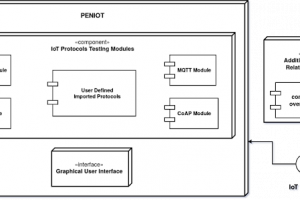
[sc name=”ad_1″] PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by...
[sc name=”ad_1″] Tsunami is a general-purpose network security scanner with an extensible plugin system for detecting high severity vulnerabilities...
[sc name=”ad_1″] Shhgit finds secrets and sensitive files across GitHub code and Gists committed in near real time by listening to the GitHub...
[sc name=”ad_1″] Run Hashcat on Google Colab with session restore capabilities with Google Drive. Usage Go to the link below to open a copy of the...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
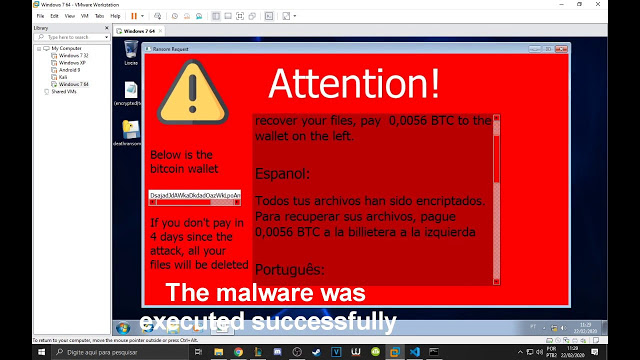
[sc name=”ad_1″] What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a...