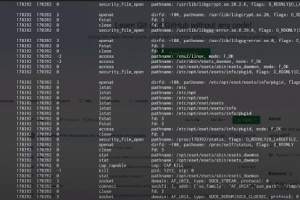
[sc name=”ad_1″] Tracee is a lightweight and easy to use container and system tracing tool. It allows you to observe system calls and other system...
Search Results For - Access
[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...
[sc name=”ad_1″] An interactive command prompt that executes commands through proxychains and automatically logs them on a Cobalt Strike team...
[sc name=”ad_1″] The Instagram OSINT Tool gets a range of information from an Instagram account that you normally wouldn’t be able to get...
[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
[sc name=”ad_1″] A (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which...
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
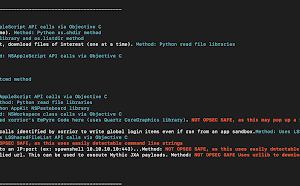
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...