CrunchRAT currently supports the following features: File upload File download Command execution It is currently single-threaded (only one task at a time), but...
Search Results For - Access
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
This scam email is nearly well designed. The scammers are using a template system to create individualized reports with specific recipient data. This works...
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
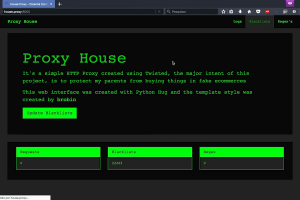
Protect your parents from phishing, HTTP proxy focused on block phishing URL’s Install git clone cd HouseProxy/ pip install -r requeriments.txt Config...
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
Critically, both OS updates address the KRACK Wi-Fi vulnerability for any devices. It is a dangerous vulnerability in the WPA2 Wi-Fi assurance standard that...
FireEye’s Innovation and Custom Engineering (ICE) team released a tool called GoCrack that allows red teams to efficiently manage password cracking tasks...