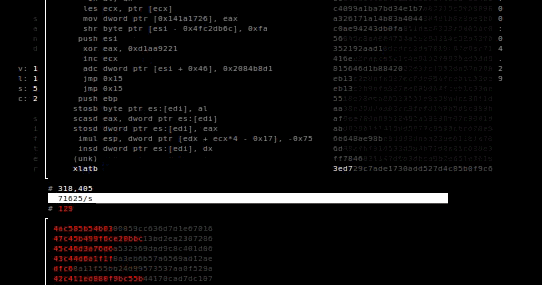
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
Search Results For - Access
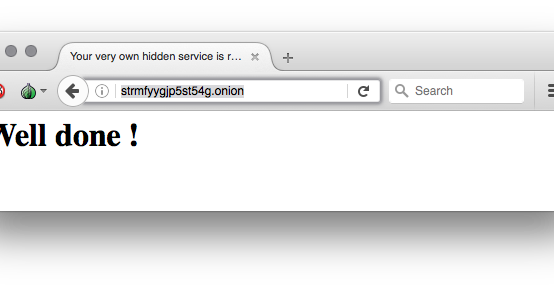
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
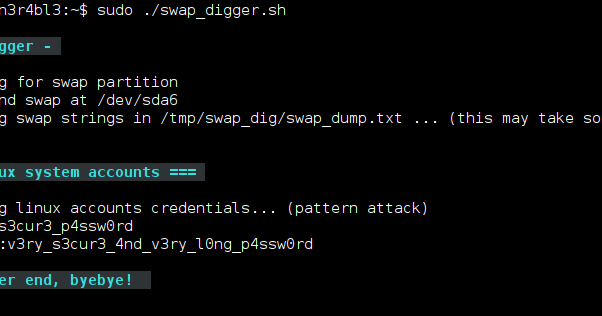
swap_digger is a bash script used to automate Linux swap analysis for post-exploitation or forensics purpose. It automates swap extraction and searches for...
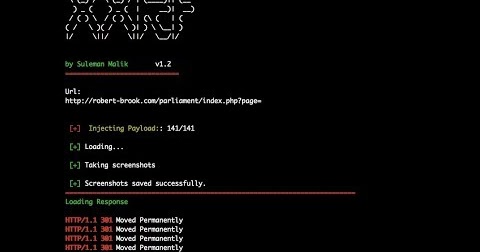
What is SSRF vulnerability? Server Side Request Forgery (SSRF) is a type of vulnerability class where attacker sends crafted request from a vulnerable web...
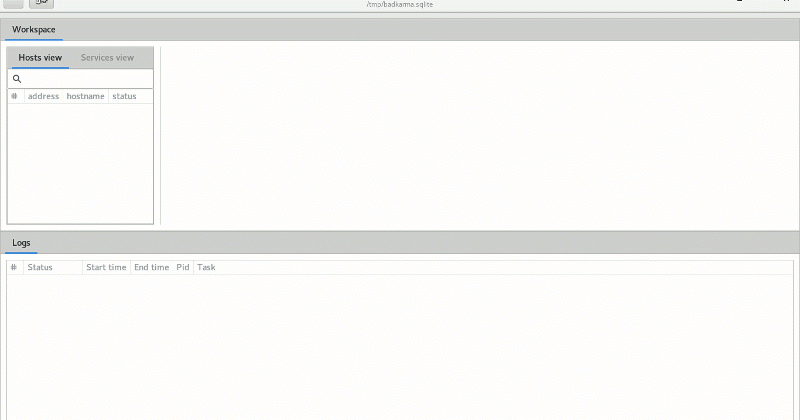
badKarma is a python3 GTK+ network infrastructure penetration testing toolkit. badKarma aim to help the tester in all the penetration testing phases...
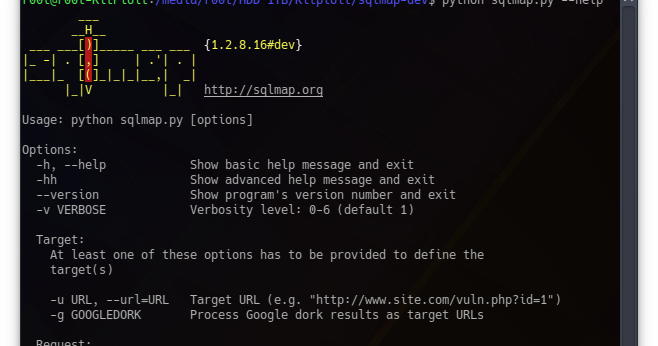
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
What is Cindicator? Cindicator fuses together machine learning and market analysis for asset management and financial analytics. The Cindicator team dubs this...
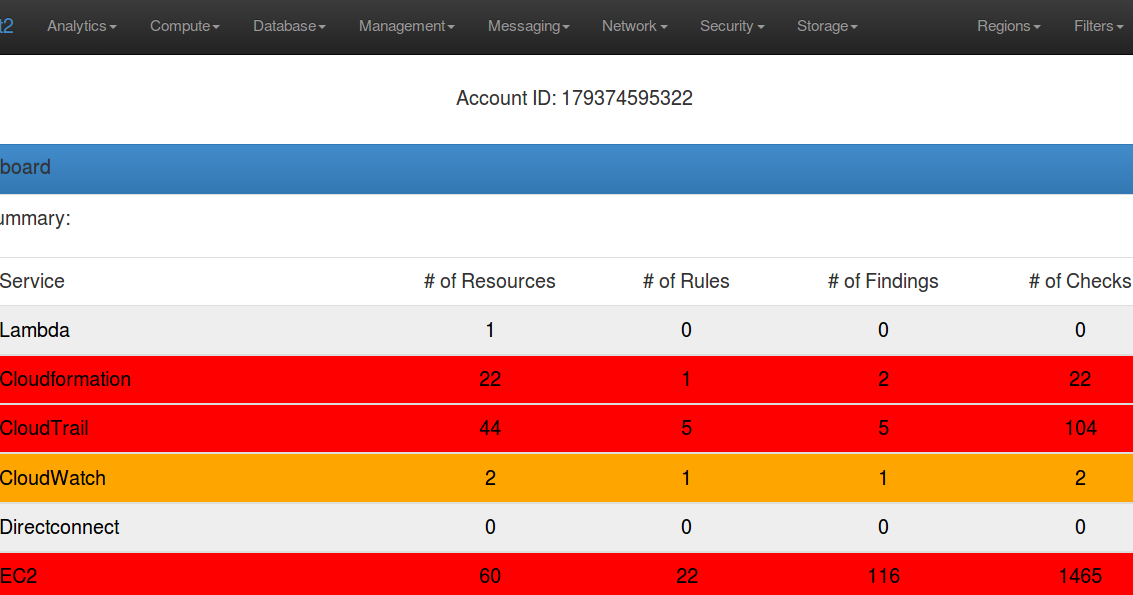
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...