Tumblr today published a report admitting the presence of a security vulnerability in its website that could have allowed hackers to steal login credentials...
Search Results For - Access Token
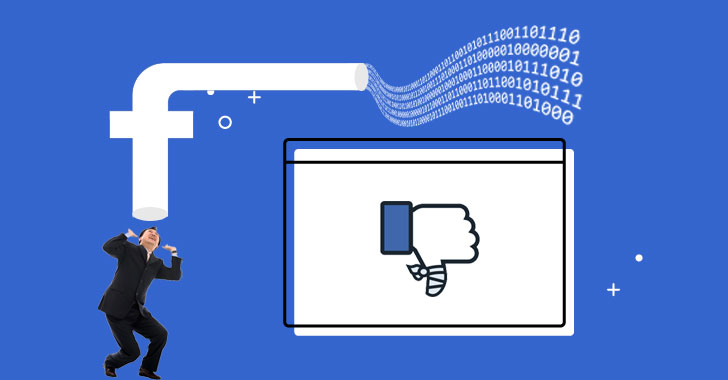
Late last month Facebook announced its worst-ever security breach that allowed an unknown group of hackers to steal secret access tokens for millions of...
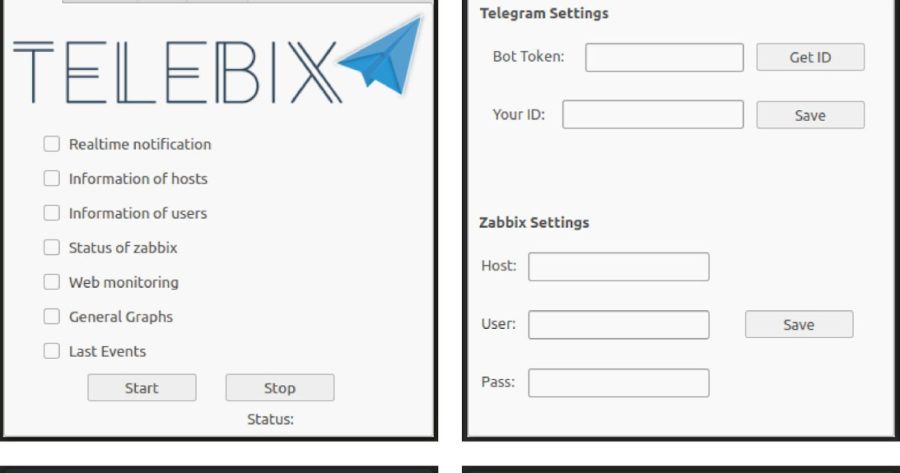
Telebix is an application that communicates with a Bot on the Telegram to receive commands and send information from an infrastructure monitored by Zabbix...
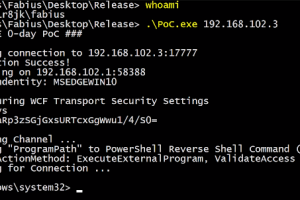
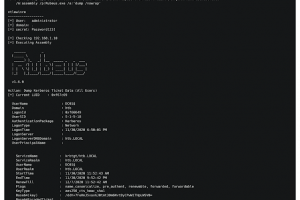
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
Blockchain.info is a bitcoin cryptocurrency wallet and block explorer service. Started in August 2011, the service presents information on new transactions...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] Credential Dumping Tool for SolarWinds Orion Blog post: Credit to @asolino, @gentilkiwi, and @skelsec for helping me figuring out...
[sc name=”ad_1″] A sharpen version of CrackMapExec. This tool is made to simplify penetration testing of networks and to create a swiss army knife...