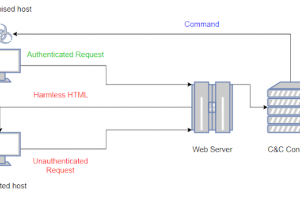
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
Search Results For - Access Token
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
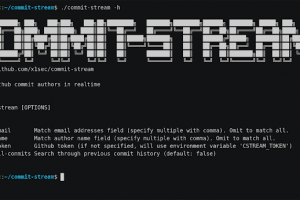
[sc name=”ad_1″] commit-stream drinks commit logs from the Github event firehose exposing the author details (name and email address) associated...
[sc name=”ad_1″] Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x) This script use...
[sc name=”ad_1″] Shhgit finds secrets and sensitive files across GitHub code and Gists committed in near real time by listening to the GitHub...
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] Late last year when an unknown group of hackers stole secret access tokens for millions of Facebook accounts by taking advantage...
[sc name=”ad_1″] Facebook’s latest screw-up — a programming bug in Facebook website accidentally gave 1,500 third-party apps access to the...
[sc name=”ad_1″] Here we have great news for all bug bounty hunters. Now you can get paid up to $40,000 for finding and responsibly reporting...