[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
Search Results For - AWS EC2
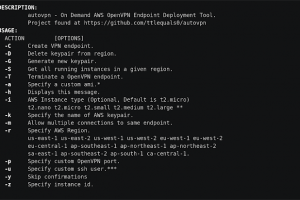
[sc name=”ad_1″] Script that allows the easy creation of OpenVPN endpoints in any AWS region. To create a VPN endpoint is done with a single...
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
[sc name=”ad_1″] Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk...
[sc name=”ad_1″] With countless web apps and online services launching every day, there is an increasing demand for cloud developers. This exciting...
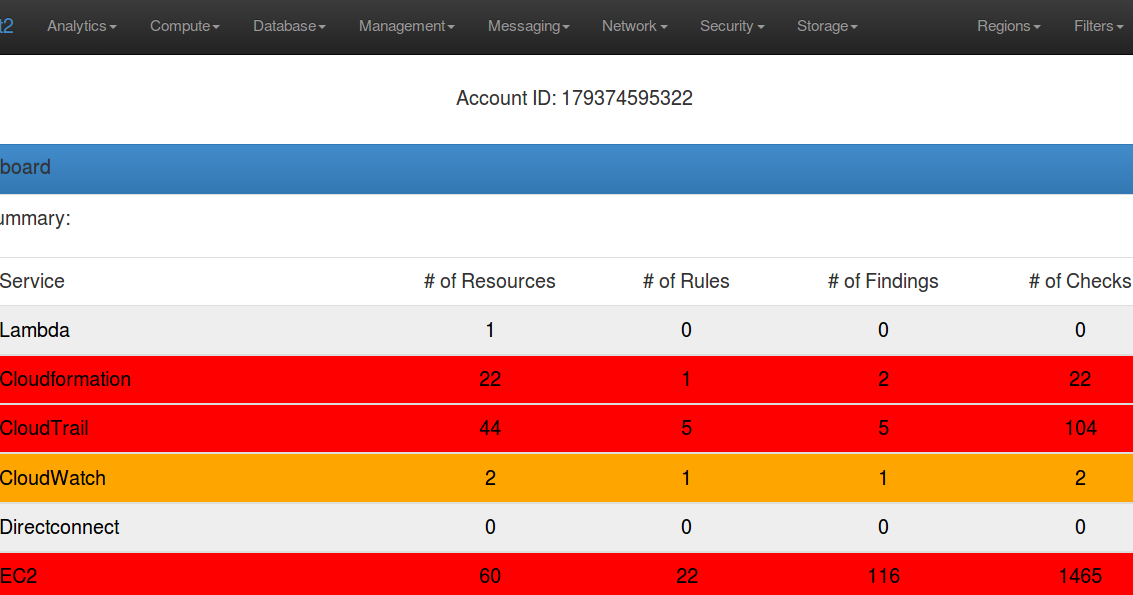
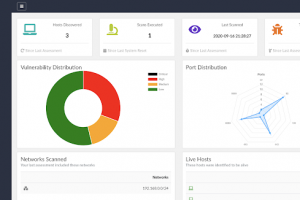
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
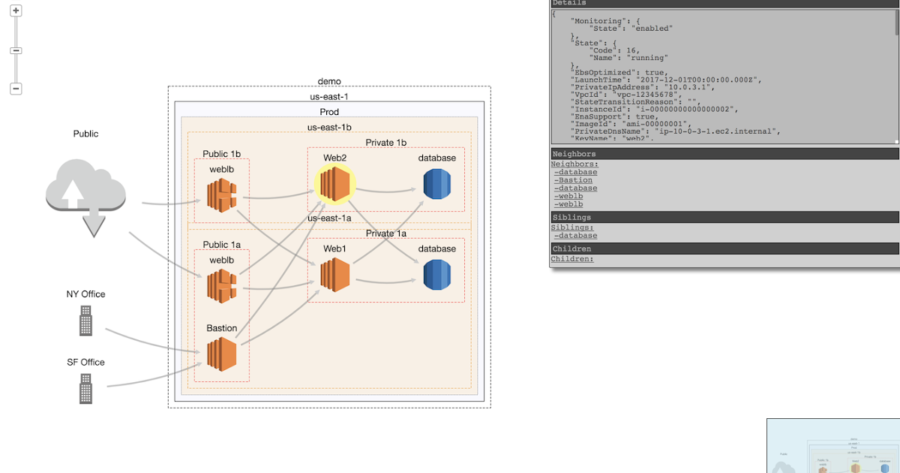
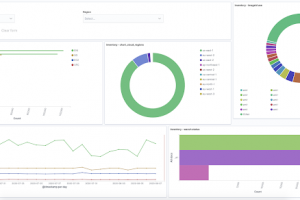
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
[sc name=”ad_1″] Dagobah is an open source tool written in python to automate the internal threat intelligence generation, inventory collection and...
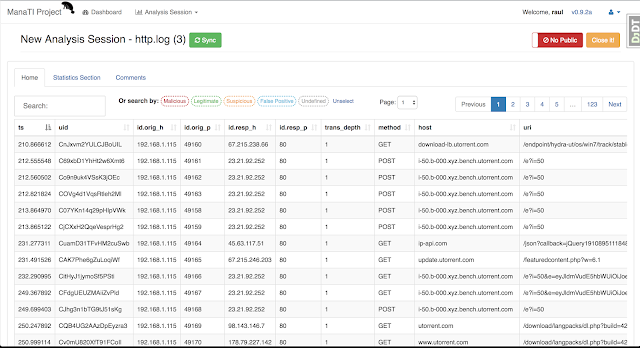
[sc name=”ad_1″] Machine Learning for Threat Intuitive Analysis The goal of the ManaTI project is to develop machine learning techniques to assist...