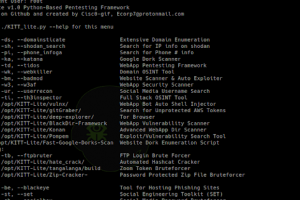
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
Search Results For - /Vulnerability
[sc name=”ad_1″] 2020-06-06 Update: this trick no longer works on the latest builds of Windows 10 Insider Preview. This means that, although it...
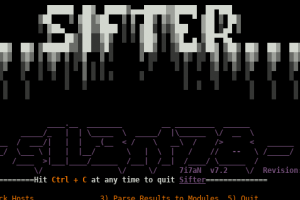
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to...
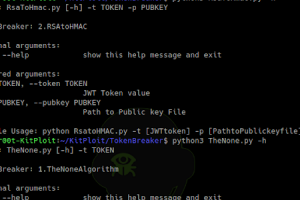
[sc name=”ad_1″] Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None Algorithm RSAtoHMAC Refer to this link about...
[sc name=”ad_1″] All-in-one tool for managing vulnerability reports Why The goal of Purify to be an easy-in-use and efficient tool to simplify a...
[sc name=”ad_1″] AutoRDPwn is a post-exploitation framework created in Powershell, designed primarily to automate the Shadow attack on Microsoft...
[sc name=”ad_1″] A list of useful payloads and bypasses for Web Application Security. Feel free to improve with your payloads and techniques ...
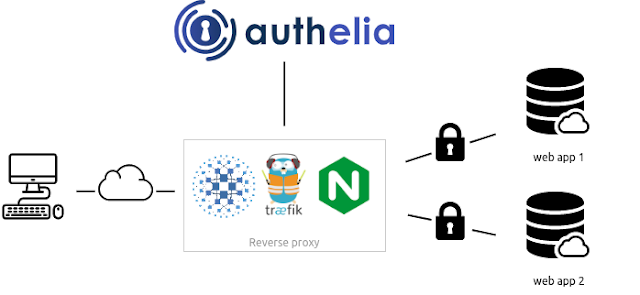
[sc name=”ad_1″] Authelia is an open-source authentication and authorization server providing 2-factor authentication and single sign-on (SSO) for...
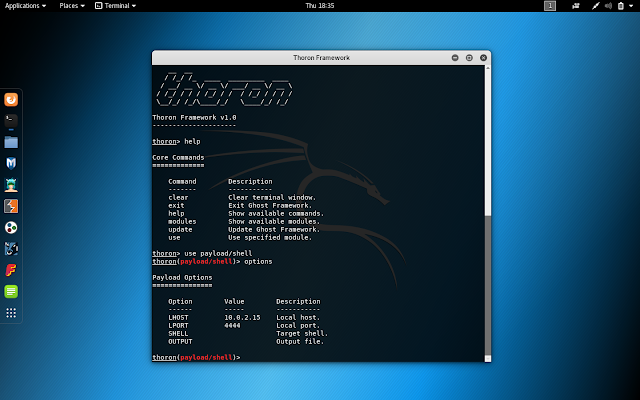
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
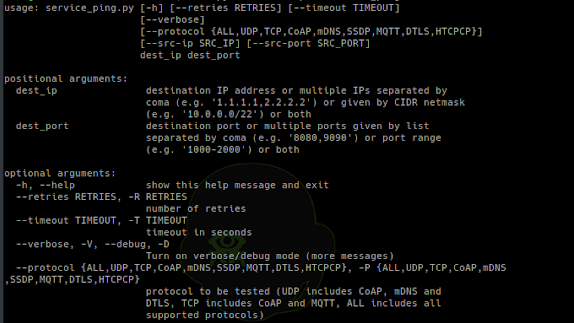
[sc name=”ad_1″] Set of tools for security testing of Internet of Things devices using protocols like: CoAP, DTLS, HTCPCP, mDNS, MQTT, SSDP...