[sc name=”ad_1″] For the most up-to-date information on Anchore Engine, Anchore CLI, and other Anchore software, please refer to the Anchore...
Search Results For - /Vulnerability
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] Bluescan is a open source project by Sourcell Xu from DBAPP Security HatLab. Anyone may redistribute copies of bluescan to anyone...
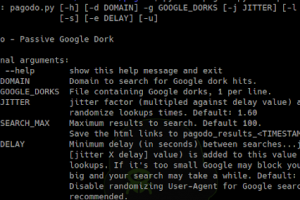
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
[sc name=”ad_1″] Detect XSS vulnerability in Web Applications Screenshots Easy Installation As simple as below, Just one line of code: curl -L -s...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] Oralyzer, a simple python script, capable of identifying the open redirection vulnerability in a website. It does that by fuzzing...
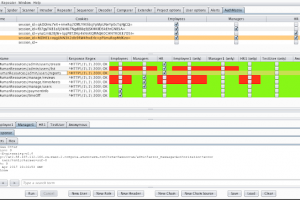
[sc name=”ad_1″] AuthMatrix is an extension to Burp Suite that provides a simple way to test authorization in web applications and web services...
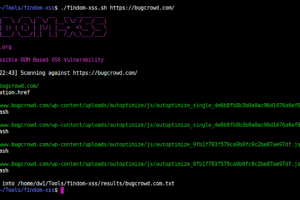
[sc name=”ad_1″] FinDOM-XSS is a tool that allows you to finding for possible and/ potential DOM based XSS vulnerability in a fast manner...
[sc name=”ad_1″] Threat Dragon is a free, open-source, cross-platform threat modeling application including system diagramming and a rule engine to...