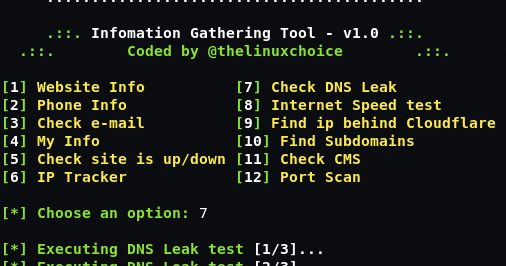
InfoG is a Shellscript to perform Information Gathering. Features Check Website info Check Phone info IP Tracker Check Valid E-mail Check if site is Up/Down Check...
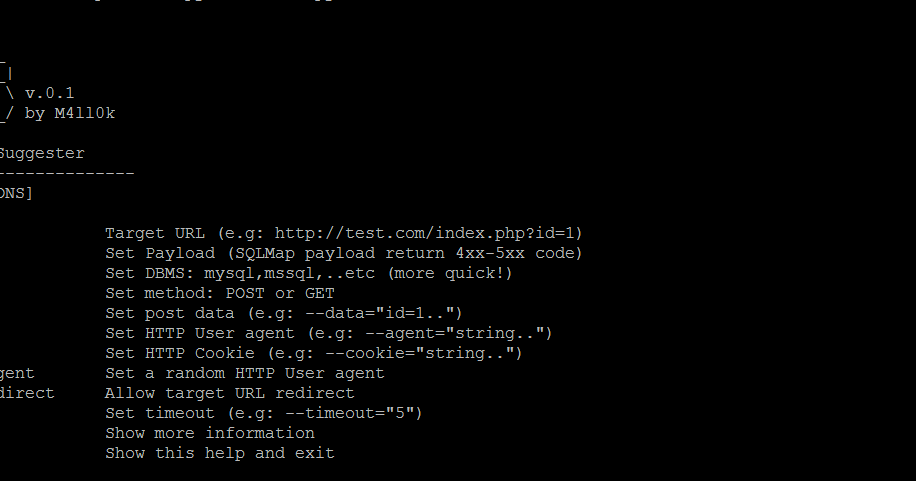
Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code. Screen Installation $ git clone atlas $ cd...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4.5 How it...
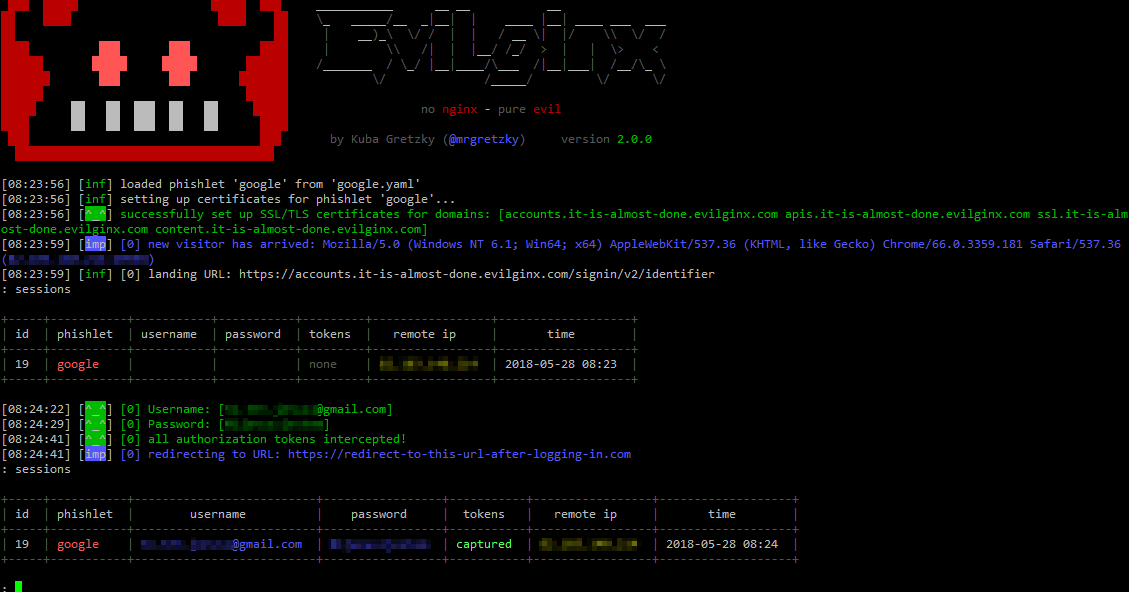
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication...
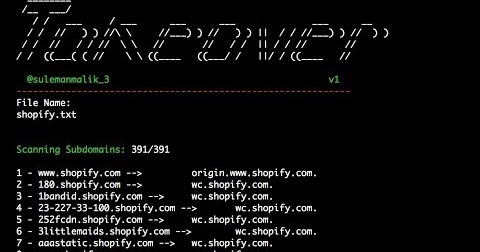
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external services are...
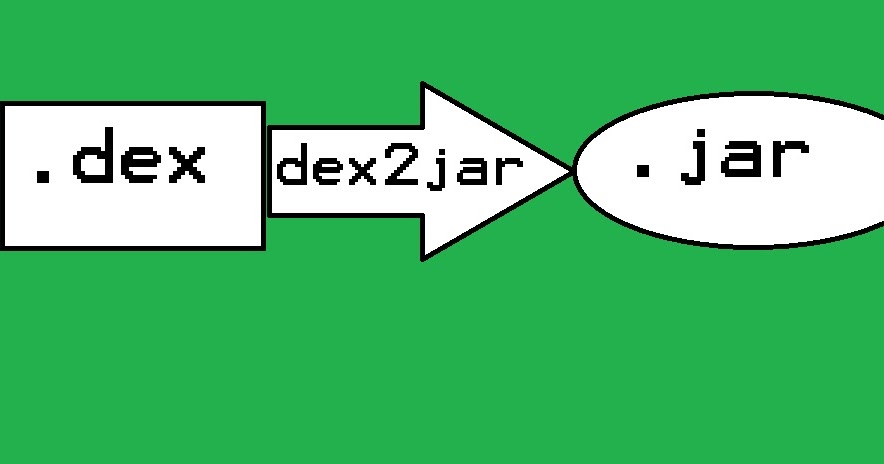
dex2jar Tools to work with android .dex and java .class files dex-reader/writer: Read/write the Dalvik Executable (.dex) file. It has a light weight API similar with ASM...
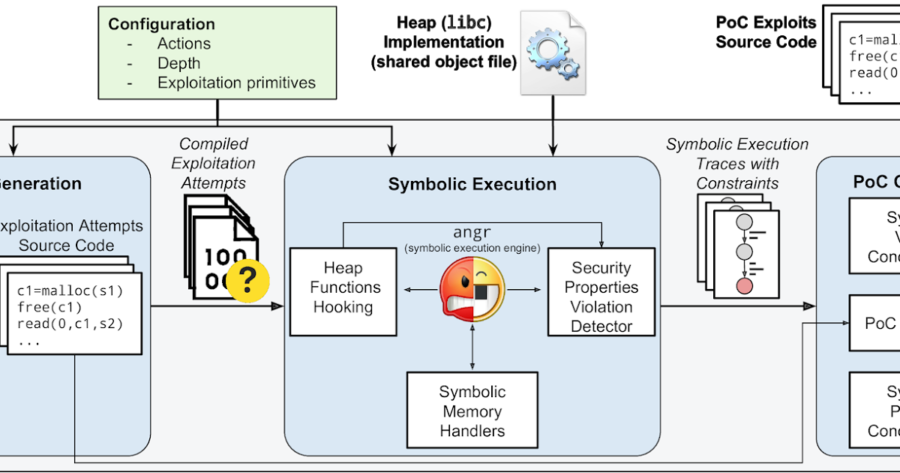
HeapHopper is a bounded model checking framework for Heap-implementations. Setup sudo apt update && sudo apt install build-essential python-dev virtualenvwrapper...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the latest version...
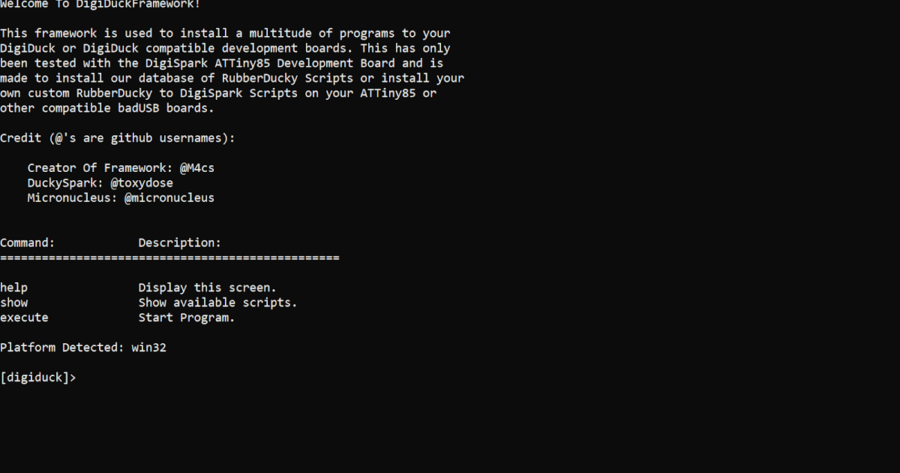
Framework for Digiduck Development Boards running ATTiny85 processors and micronucleus bootloader! Roadmap: Plan to implement a command for Duckyspark translation within...
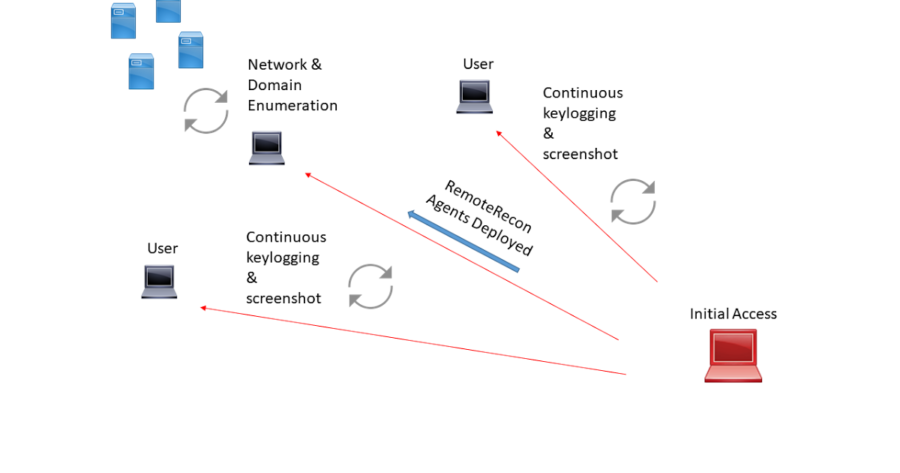
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often times as...