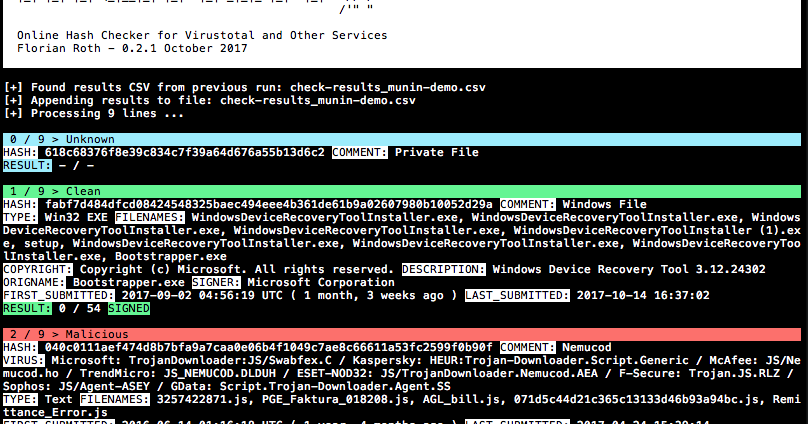
Munin is a online hash checker utility that retrieves valuable information from various online sources The current version of Munin queries the following services:...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote attacker to...
Injects C# EXE or DLL Assembly into any CLR runtime and AppDomain of another process. The injected assembly can then access static instances of the injectee...
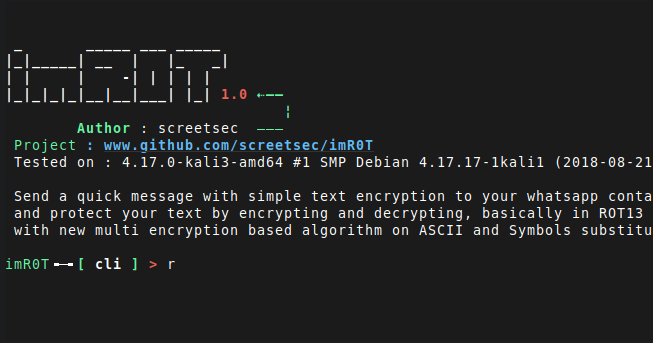
imR0T: Send a quick message with simple text encryption to your whatsapp contact and protect your text by encrypting and decrypting, basically in ROT13 with new multi...
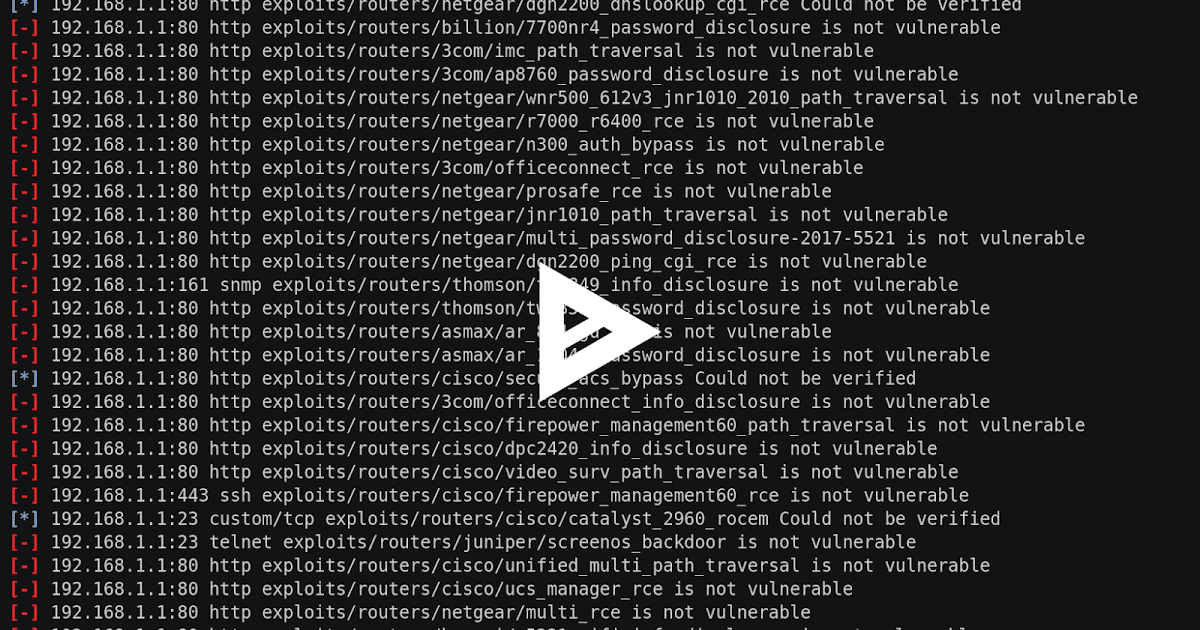
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
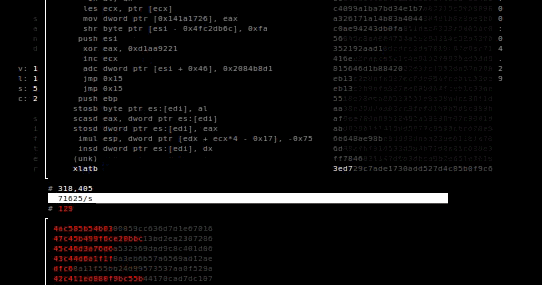
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
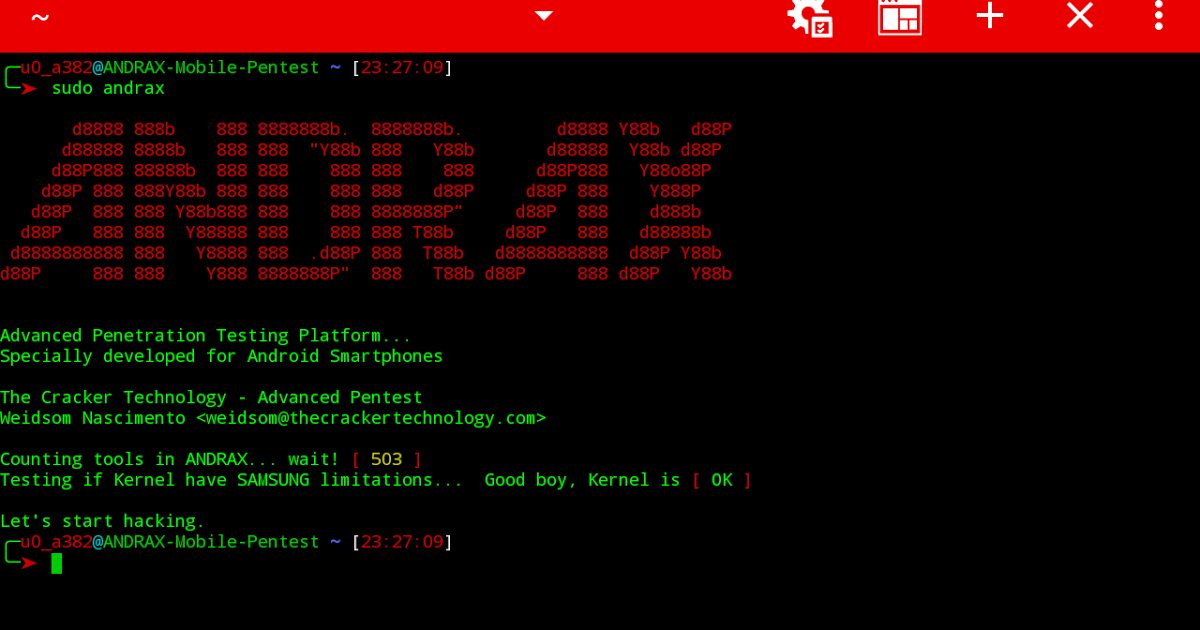
ANDRAX The first and unique Penetration Testing platform for Android smartphones What is ANDRAX ANDRAX is a penetration testing platform developed specifically for...
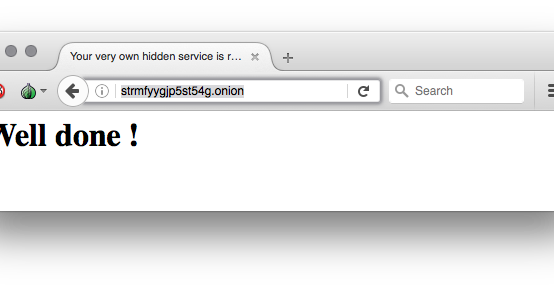
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden service...
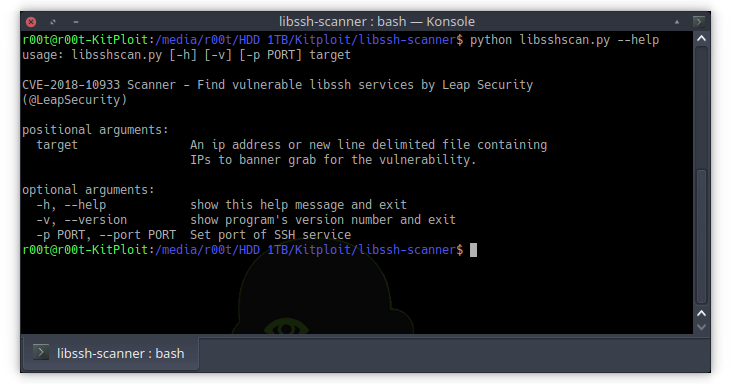
This is a python based script to identify hosts vulnerable to CVE-2018-10933. The vulnerability is present on versions of libssh 0.6+ and was remediated by a patch...
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and suspected...