[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h _____ ____ _...
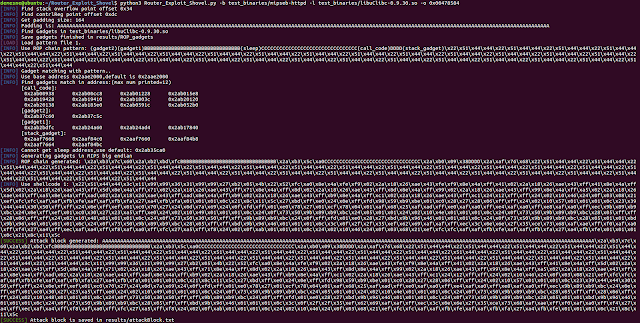
[sc name=”ad_1″] Automated Application Generation for Stack Overflow Types on Wireless Routers. Router exploits shovel is an automated application generation...
[sc name=”ad_1″] Anteater is an open framework to prevent the unwanted merging of nominated strings, filenames, binaries, depreciated functions, staging...
[sc name=”ad_1″] SKA allows you to implement a very simple and fast karma attack. You can sniff probe requests to choice the fake AP name or, if you want...
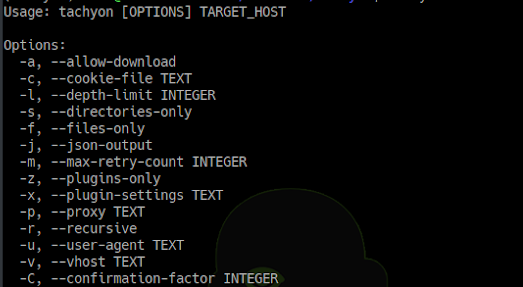
[sc name=”ad_1″] Tachyon is a fast web application security reconnaissance tool. It is specifically meant to crawl web application and look for left over or...
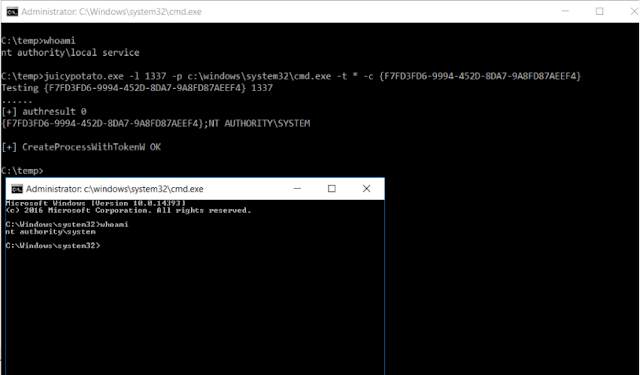
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service Accounts to...
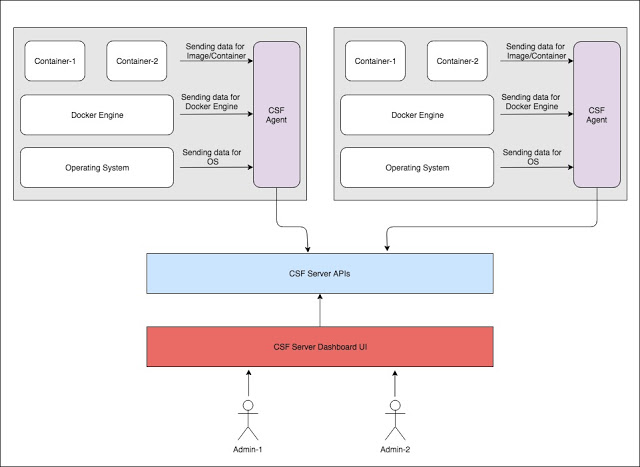
[sc name=”ad_1″] ArmourBird CSF – Container Security Framework is an extensible, modular, API-first framework build for regular security monitoring of...
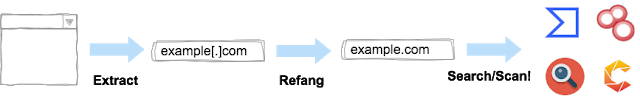
[sc name=”ad_1″] Mitaka is a browser extension for OSINT search which can: Extract & refang IoC from a selected block of text. E.g. example[.]com to...
[sc name=”ad_1″] Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments. Using the...
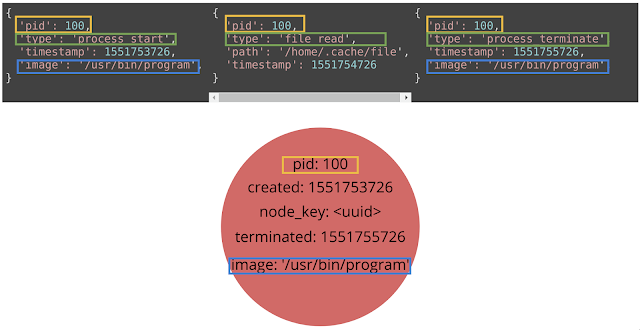
[sc name=”ad_1″] Grapl is an open source platform for Detection and Response (D&R). The position that Grapl takes is that Graphs provide a more natural...