[sc name=”ad_1″] snare – Super Next generation Advanced Reactive honEypot Super Next generation Advanced Reactive honEypot About SNARE is a web...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting known...
CentOS which stands for Community Enterprise Operating System is one of the most widely used Linux distribution available for free. It powers many web servers across the...
Hey Guys, In this video i show you How to Bypass Facebook Profile Picture Guard. Open the victim’s profile then right click on the page and click view page source. Now...
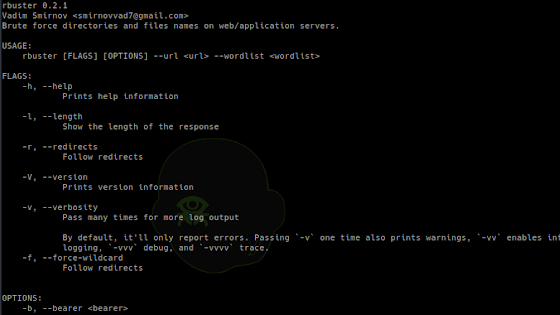
[sc name=”ad_1″] yet another dirbuster Common Command line options -a <user agent string> – specify a user agent string to send in the request -c...
[sc name=”ad_1″] An XMLRPC brute forcer targeting WordPress written in Python 3. In the context of xmlrpc brute forcing, its faster than Hydra and WpScan. It...
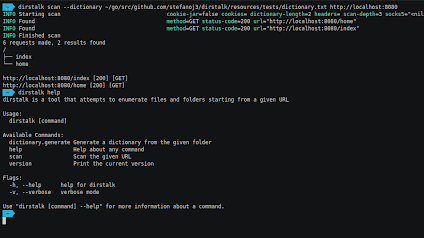
[sc name=”ad_1″] Dirstalk is a multi threaded application designed to brute force paths on web servers. The tool contains functionalities similar to the ones...
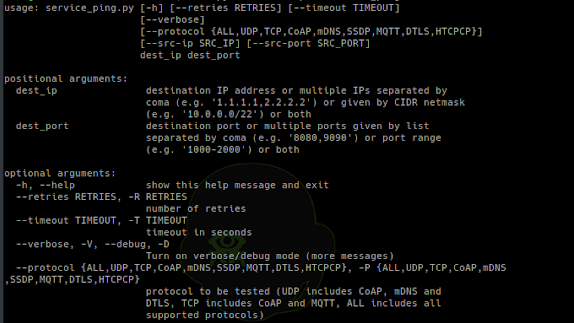
[sc name=”ad_1″] Set of tools for security testing of Internet of Things devices using protocols like: CoAP, DTLS, HTCPCP, mDNS, MQTT, SSDP. Installation:...
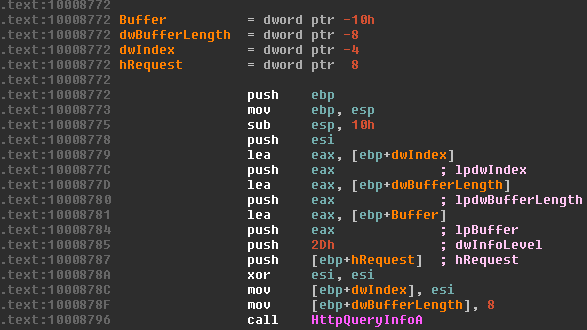
[sc name=”ad_1″] IDA PRO Auto-Renaming Plugin With Tagging Support Features 1. Auto-renaming dummy-named functions, which have one API call or jump to the...
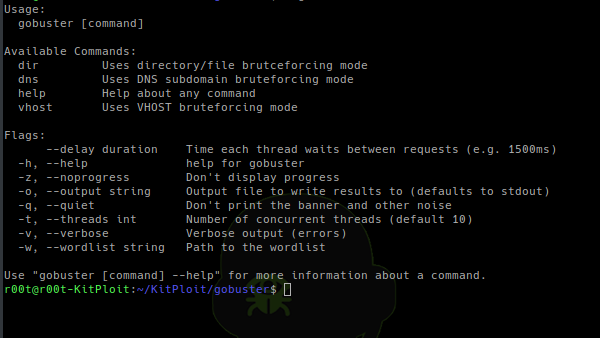
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual Host...