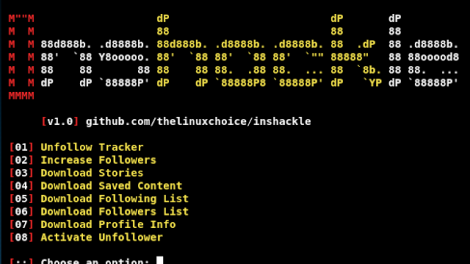
[sc name=”ad_1″] Instagram hacks: Track unfollowers, Increase your followers, Download Stories, etc Features: Unfollow Tracker Increase Followers Download:...
[sc name=”ad_1″] In this malware, are used some techniques to try bypass the AVs, VMs, and Sandboxes, with only porpuse to learning more. I’m not...
[sc name=”ad_1″] The Forerunner library is a fast, lightweight, and extensible networking library created to aid in the development of robust network centric...
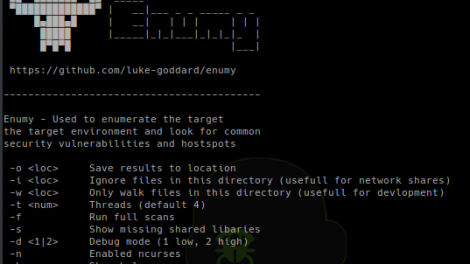
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running enumy...
[sc name=”ad_1″] Bing-ip2hosts is a Bing.com web scraper to discover hostnames by IP address. Description Bing-ip2hosts is a Bing.com web scraper that...
[sc name=”ad_1″] Please note: We take Vault’s security and our users’ trust very seriously. If you believe you have found a security issue in...
[sc name=”ad_1″] ANDRAX is a Penetration Testing platform developed specifically for Android smartphones, ANDRAX has the ability to run natively on Android...
[sc name=”ad_1″] ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will give you a...
[sc name=”ad_1″] All-in-one tool for managing vulnerability reports Why The goal of Purify to be an easy-in-use and efficient tool to simplify a workflow of...
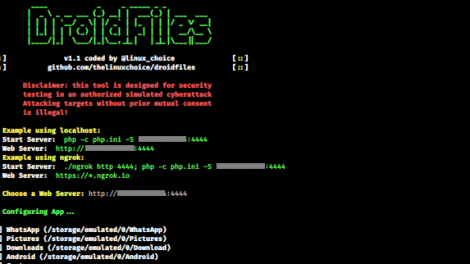
[sc name=”ad_1″] Get files from Android directories, internal and external storage (Pictures, Downloads, Whatsapp, Videos, …) Legal disclaimer: Usage...