[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read usernames from...
[sc name=”ad_1″] A proof-of-concept for WebRTC signaling using sound. Works with all devices that have microphone + speakers. Runs in the browser. Nearby...
[sc name=”ad_1″] Gitjacker downloads git repositories and extracts their contents from sites where the .git directory has been mistakenly uploaded. It will...
[sc name=”ad_1″] Nasha is a Virtual Machine for .NET files and its runtime was made in C++/CLI Installation git clone --recurse cd NashaVMNashaVM nuget...
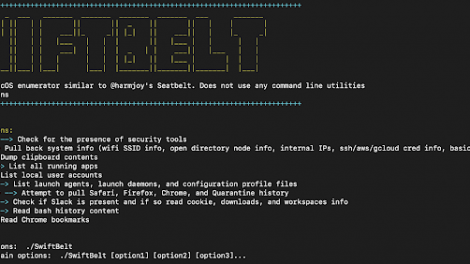
[sc name=”ad_1″] SwiftBelt is a macOS enumerator inspired by @harmjoy’s Windows-based Seatbelt enumeration tool. SwiftBelt does not utilize any command...
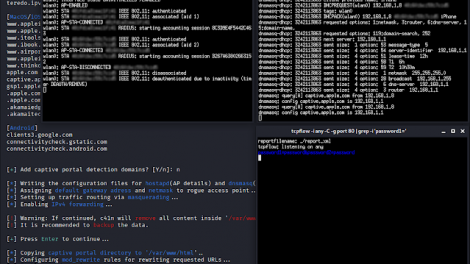
[sc name=”ad_1″] c41n is an automated Rogue Access Point setup tool. c41n provides automated setup of several types of Rogue Access Points, and Evil Twin...
[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and it’s safe...
[sc name=”ad_1″] GHunt is an OSINT tool to extract a lot of informations of someone’s Google Account email. It can currently extract : Owner’s...
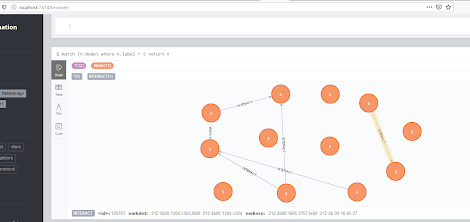
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a PhD...
[sc name=”ad_1″] Lockphish it’s the first tool (07/04/2020) for phishing attacks on the lock screen, designed to grab Windows credentials, Android PIN...