CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files. CuckooDroid brigs to cuckoo the capabilities of...
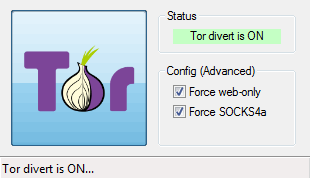
Tallow is a small program that redirects all outbound traffic from a Windows machine via the Tor anonymity network. Any traffic that cannot be handled by Tor, e.g. UDP...
A British teenager has admitted trying to hack into the computers of senior US government officials, including the director of the CIA and the deputy director of the FBI...
Pirate Bay got this the hard way when users on Reddit lately complained regarding the site’s use of such miners. The website eventually backed away from the practice...
Justin Rosenstein was the inventor and engineer who created the “awesome” feature in 2007 but now worries the mental effects apps are having on people throughout the...
Another day, Another data breach disclosure. This time the popular commenting system has fallen victim to a massive security breach. Disqus, the company which provides a...
Habu is to teach (and learn) some concepts about Python and Network Hacking. These are basic functions that help with some tasks for Ethical Hacking and Penetration...
Stealing desktop telegrams has never been so easy ! Set the email and sender details of the sender and recipient and send it to the victim after compiling. How do I use...
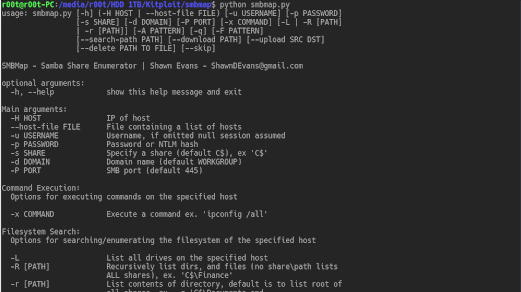
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file...
Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation dlls. dll mode: Usage: rundll32 PowerShdll,main <script>...