Legal Disclaimer: This project is made for educational and ethical testing purposes only。It is the end user’s responsibility to obey all applicable local, state and...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and even...
Google’s new Play Protect security system did not success first real-world tests, and the system was rated dead in an experiment conducted by independent German lab AV...
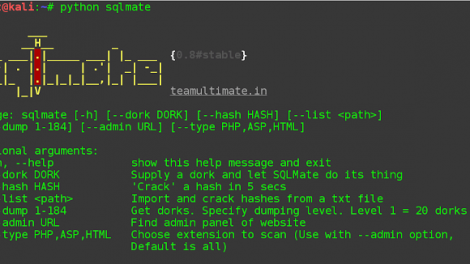
There are some features that we think SQLMap should have. Like finding admin panel of the target, better hash cracking etc. If you think the same, SQLMate is for you...
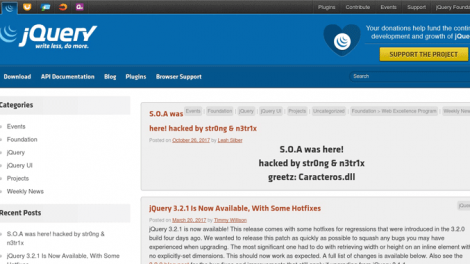
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals are...
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero currency for...
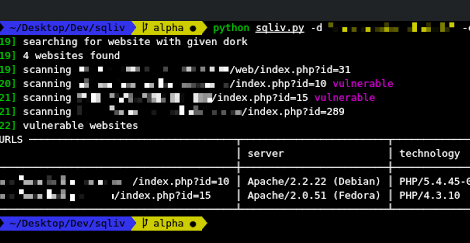
Massive SQL injection vulnerability scanner. Features multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by providing specific...
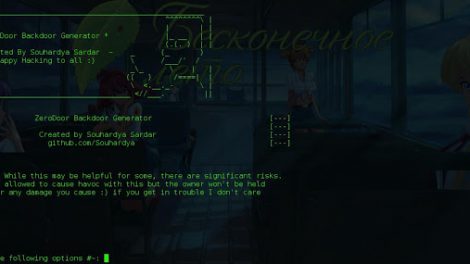
A script written lazily for generating reverse shell backdoors on the go whenever you need without any hassle for your daily penetration needs . These backdoors are not...