Relayer is an SMB relay Attack Script that automates all the necessary steps to scan for systems with SMB signing disabled and relaying authentication request to these...
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being sustainable in...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are Microsoft...
The administration of Guangzhou, center of the southern coastal province of Guangdong, began on Monday a pilot plan that creates a virtual ID card, which follows the...
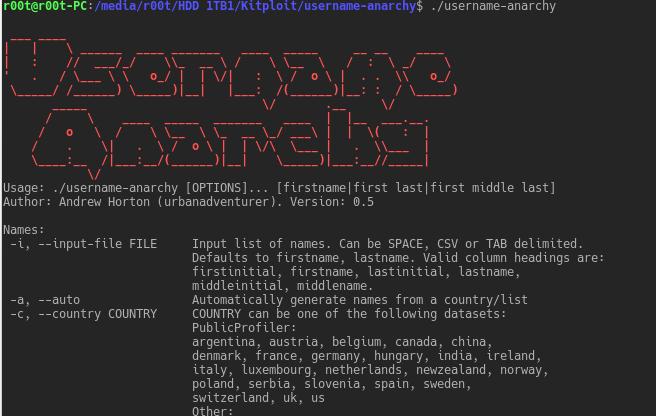
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute force...
BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard ports by...
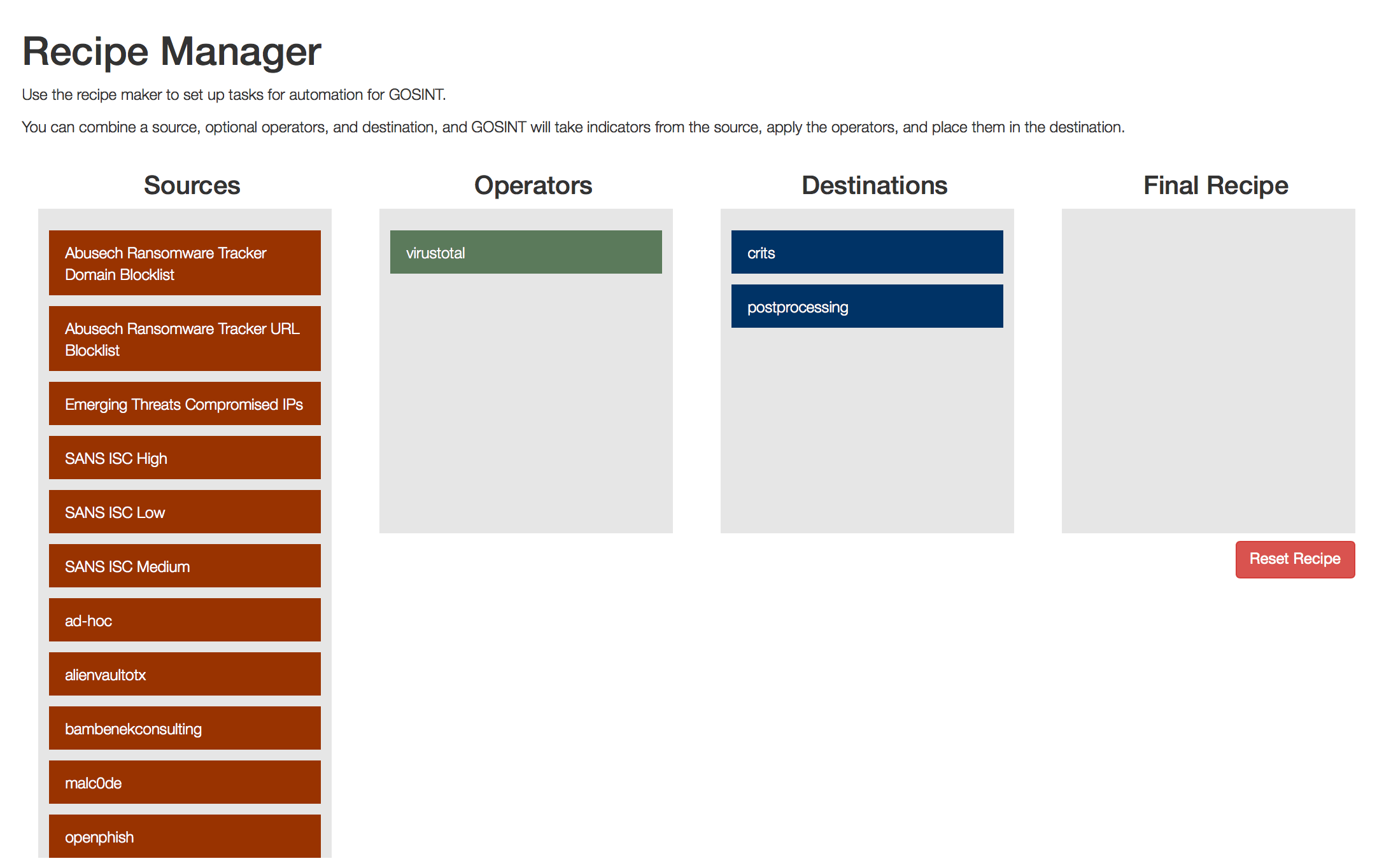
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst to...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a cryptocurrency miner...
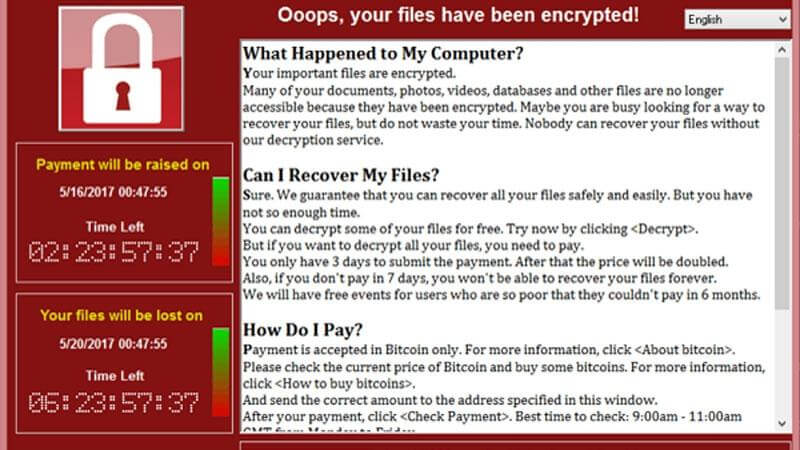
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK [Democratic...
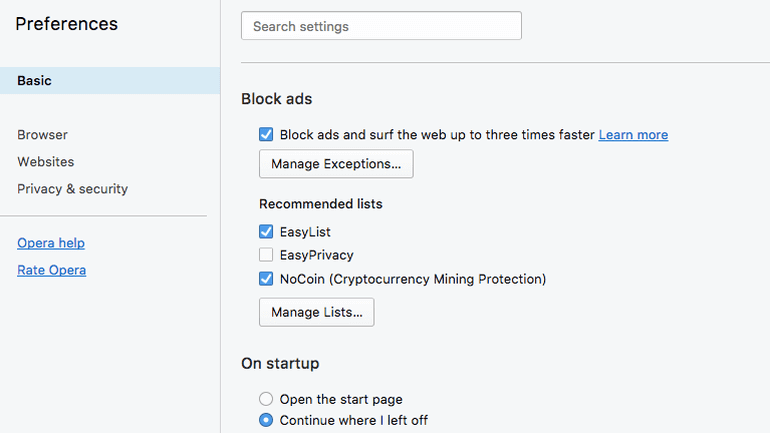
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The feature...