A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The bug is a...
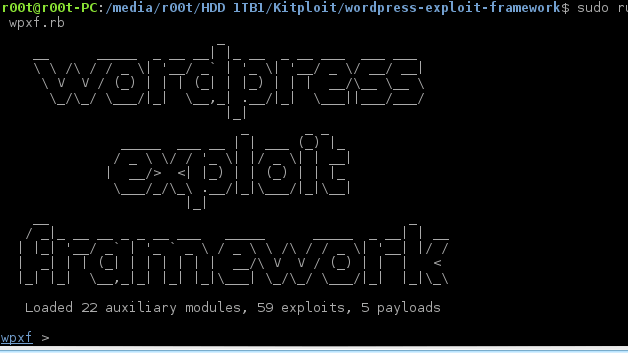
A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems. What do I need to run it? Ensure that...
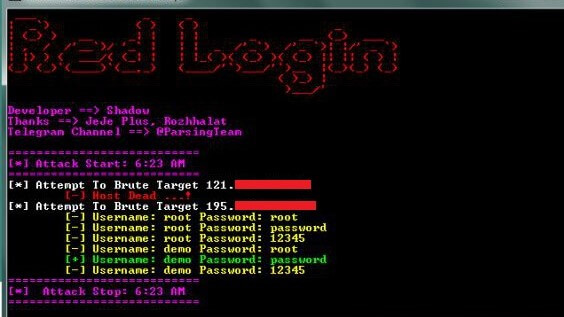
Red Login: SSH Brute-force Tools. Features: High speed and precision CLI ( Console based ) Run the arbitrary command after the attack is successful ( Default...
A breach of Forever 21 left consumer payment card data exposed to hackers, the retailer verified Thursday. The business didn’t specify how many customers had data...
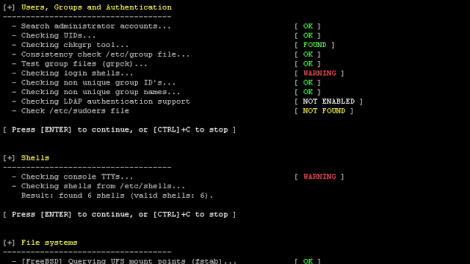
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next of...
Alphonso, a startup that retails media-viewing data, provides a plugin that listens for audio signals in shows and movies. Approximately 250 mobile entertainments and...
Chiron is an IPv6 Security Assessment Framework, written in Python and employing Scapy. It is comprised of the following modules: • IPv6 Scanner • IPv6 Local Link • IPv4...
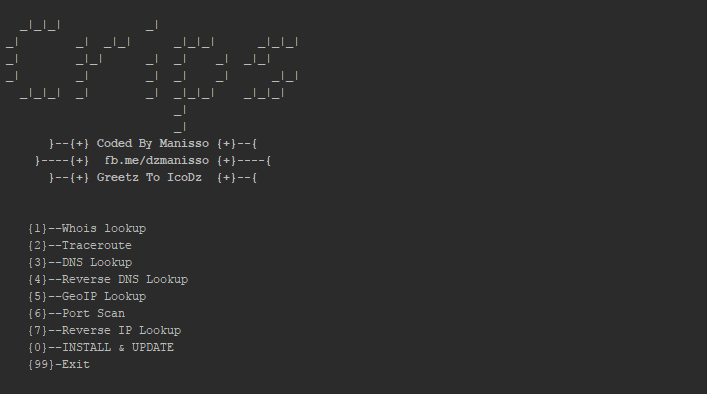
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois lookup...
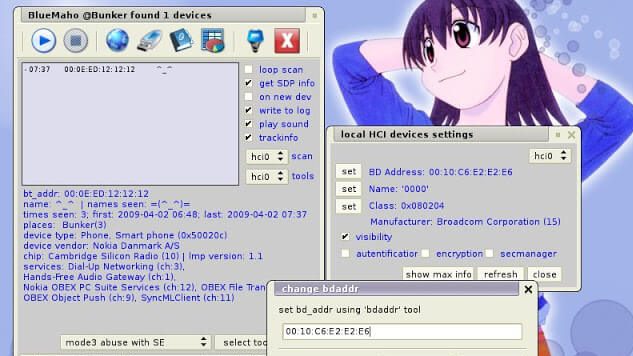
BlueMaho is GUI-shell (interface) for suite of tools for testing security of bluetooth devices. It is freeware, opensource, written on python, uses wxPyhon. It can be...
Quite recently, the founder of Mcafee company, John Mcafee, was in news when his Twitter was hacked by an unknown hacker. This hacker used John’s social media reach and...