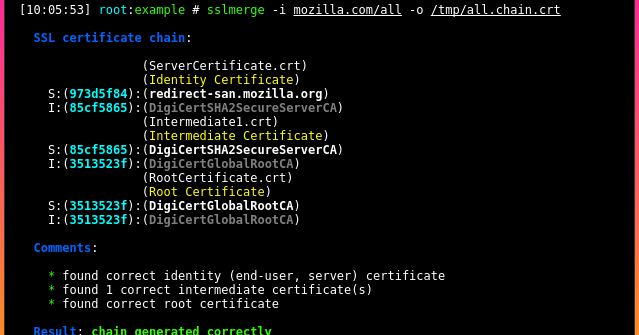
Is an open source tool to help you build a valid SSL certificate chain from the root certificate to the end-user certificate. Also can help you fix the incomplete...
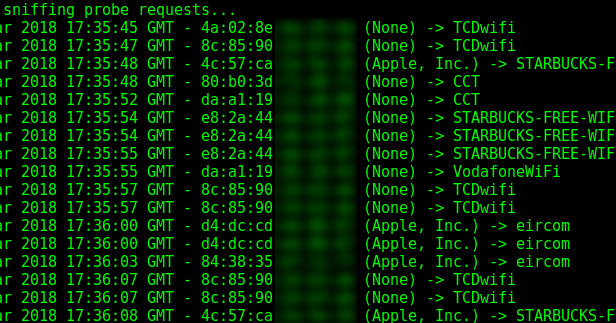
Toolkit allowing to sniff and display the Wi-Fi probe requests passing near your wireless interface. Probe requests are sent by a station to elicit information about...
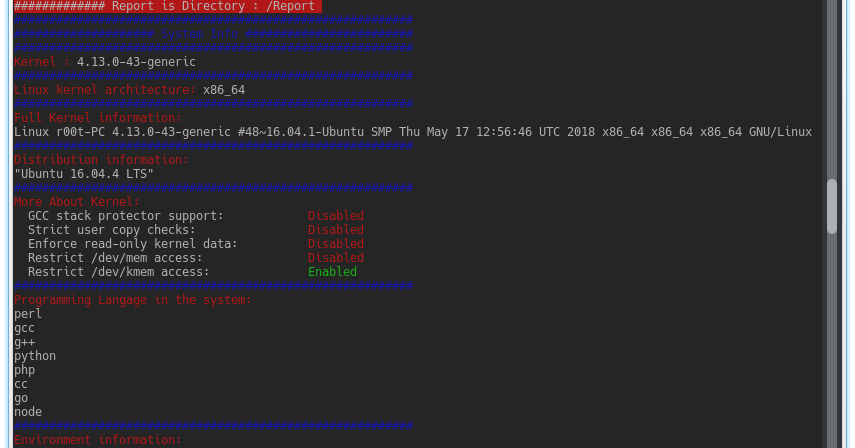
New Linux Privilege Escalation Tool. Getting Started System Information Gatherer Kernel Information Gatherer Checking Development environments on the system (Escaping...
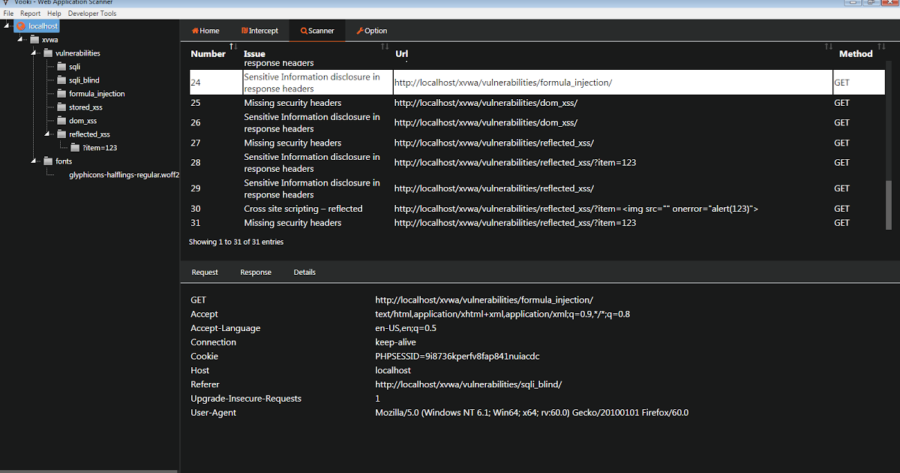
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities. Vooki...
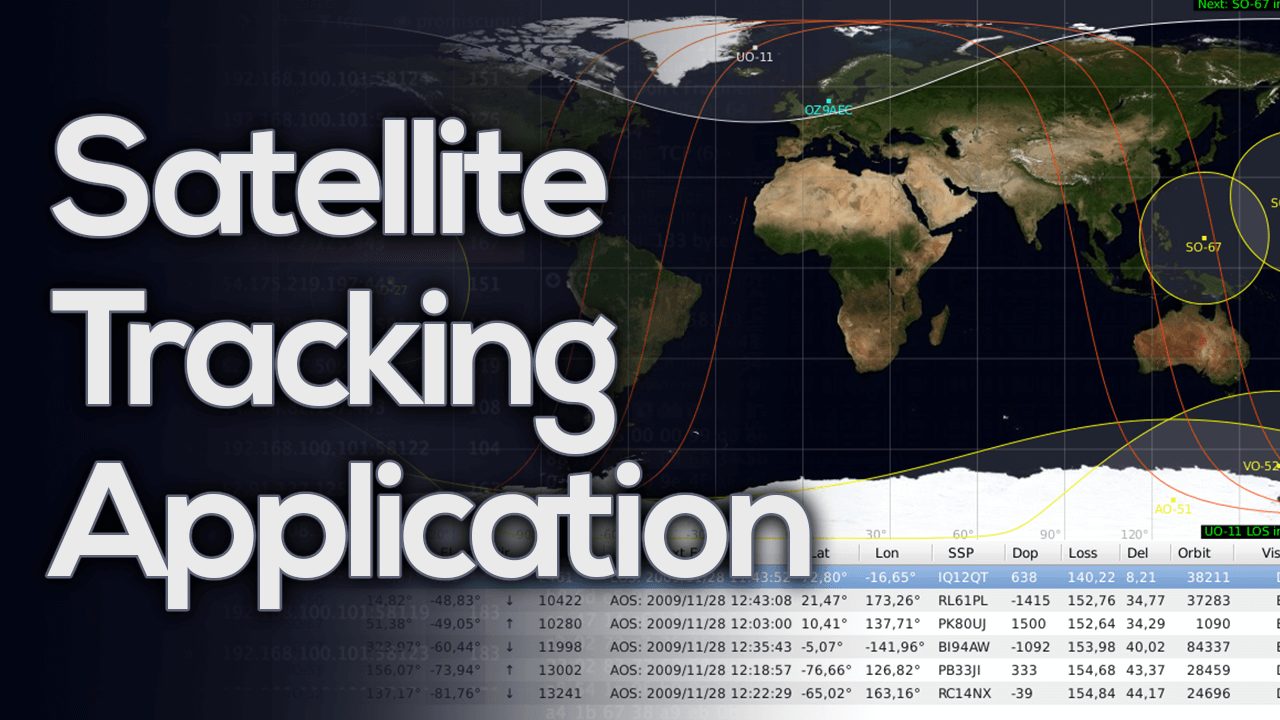
Gpredict is a real time satellite tracking and orbit prediction program for the Linux desktop. It uses the SGP4/SDP4 propagation algorithms together with NORAD two-line...
Many investors that want to enter the cryptocurrency market have never traded any form of a financial instrument before. Most of them, however, have some form of...
Hash Buster is a program which uses several APIs to perform hash lookups. Features Automatic hash type identification Supports MD5, SHA1, SHA2 Can extract & crack...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come before it...
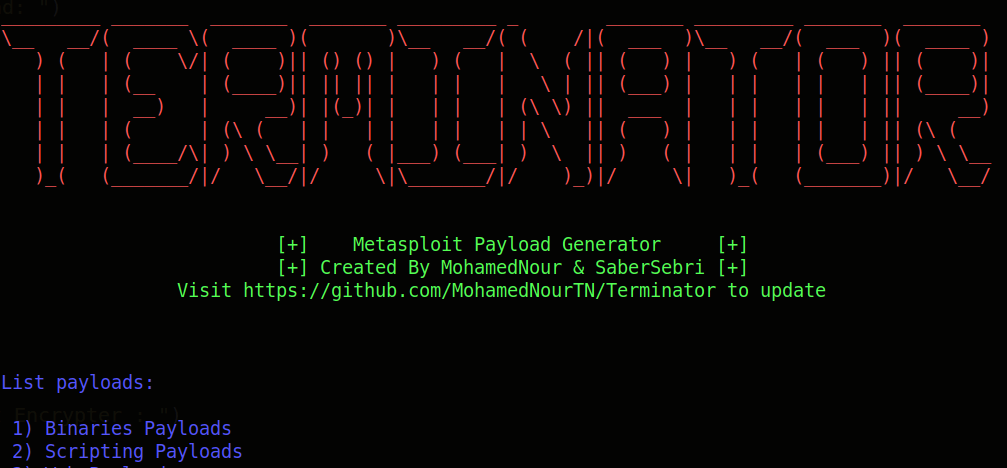
Terminator Metasploit Payload Generator. Payload List : Binaries Payloads 1) Android 2) Windows 3) Linux 4) Mac OS Scripting Payloads 1) Python 2) Perl 3) Bash Web...
pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find passwords...