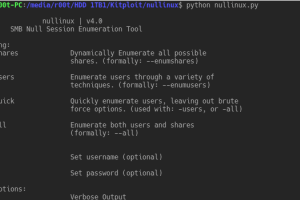
nullinux is an internal penetration testing tool for Linux that can be used to enumerate OS information, domain information, shares, directories, and users...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
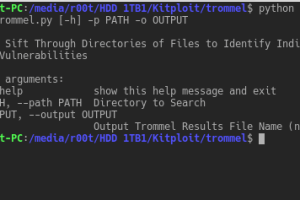
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Across the Internet, hundreds of thousands of sites rely on Google’s reCaptcha system for defense against bots (in fact, Devpost uses reCaptcha when creating a...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
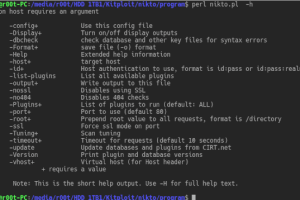
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially...
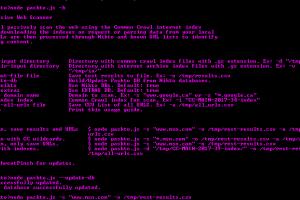
Paskto will passively scan the web using the Common Crawl internet index either by downloading the indexes on request or parsing data from your local system...
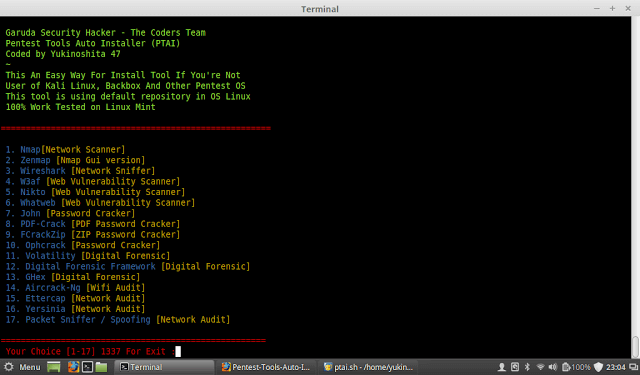
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
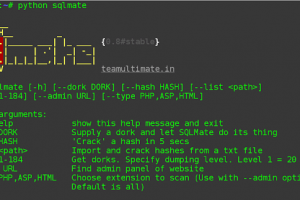
There are some features that we think SQLMap should have. Like finding admin panel of the target, better hash cracking etc. If you think the same, SQLMate is...
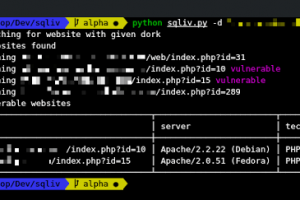
Massive SQL injection vulnerability scanner. Features multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by...