Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
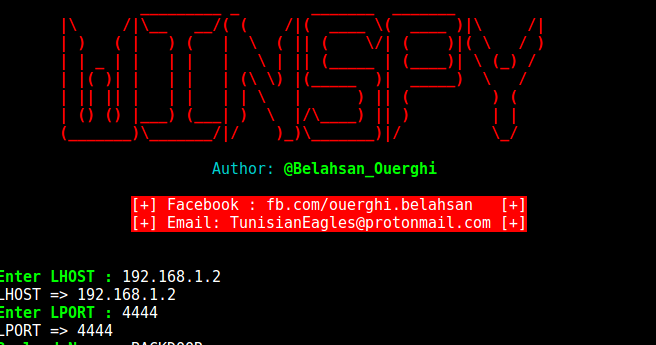
WinSpy: Windows Reverse Shell Backdoor Creator With ip poisener. Dependencies 1 – metasploit-framework 2 – xterm 3 – apache2 4 –...
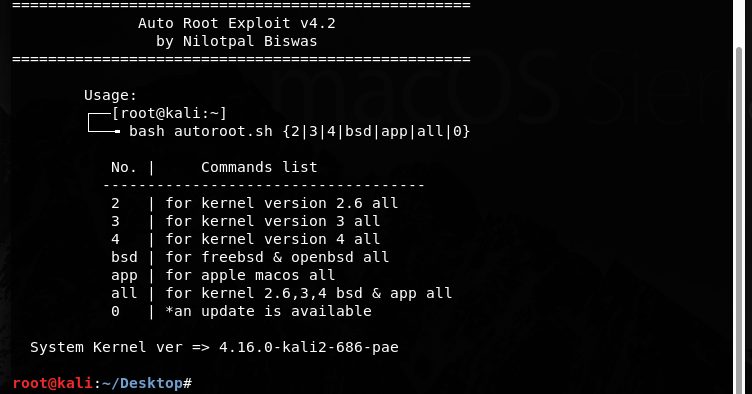
Auto Root Exploit Tool Author : Nilotpal Biswas Facebook : Twitter : USAGE : for kernel version 2.6 all bash autoroot.sh 2 for kernel version 3 all bash...
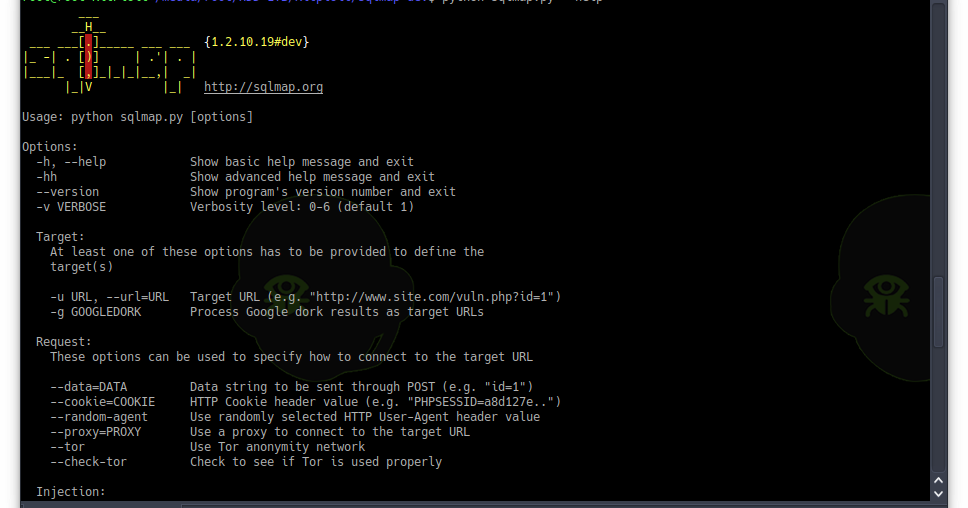
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
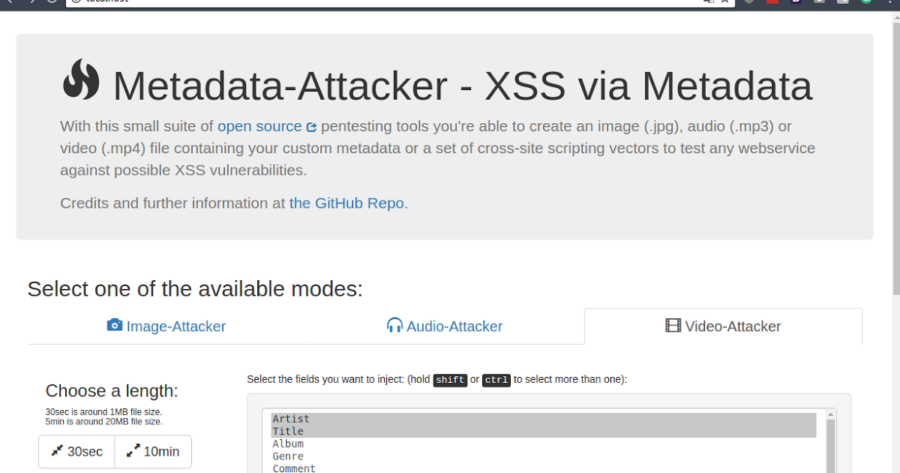
Metadata-Attacker or a set of cross-site scripting vectors to test any webservice against possible XSS vulnerabilities when displaying unfiltered meta datWith...
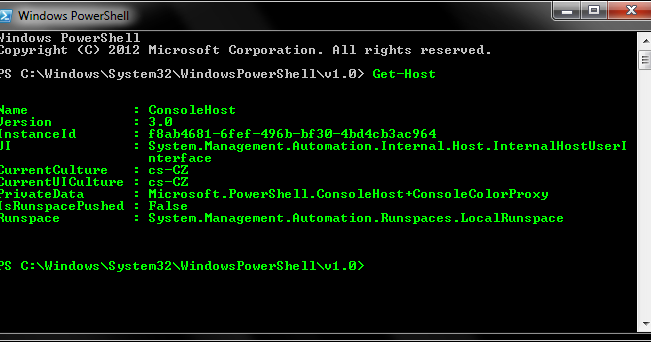
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
Injects C# EXE or DLL Assembly into any CLR runtime and AppDomain of another process. The injected assembly can then access static instances of the injectee...
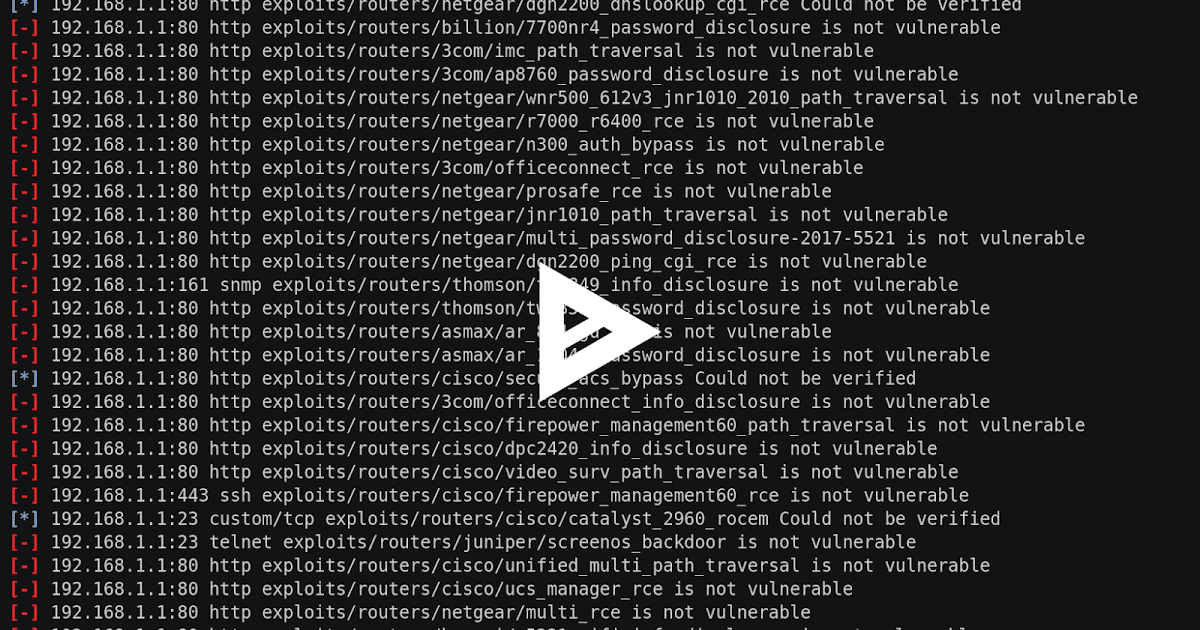
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
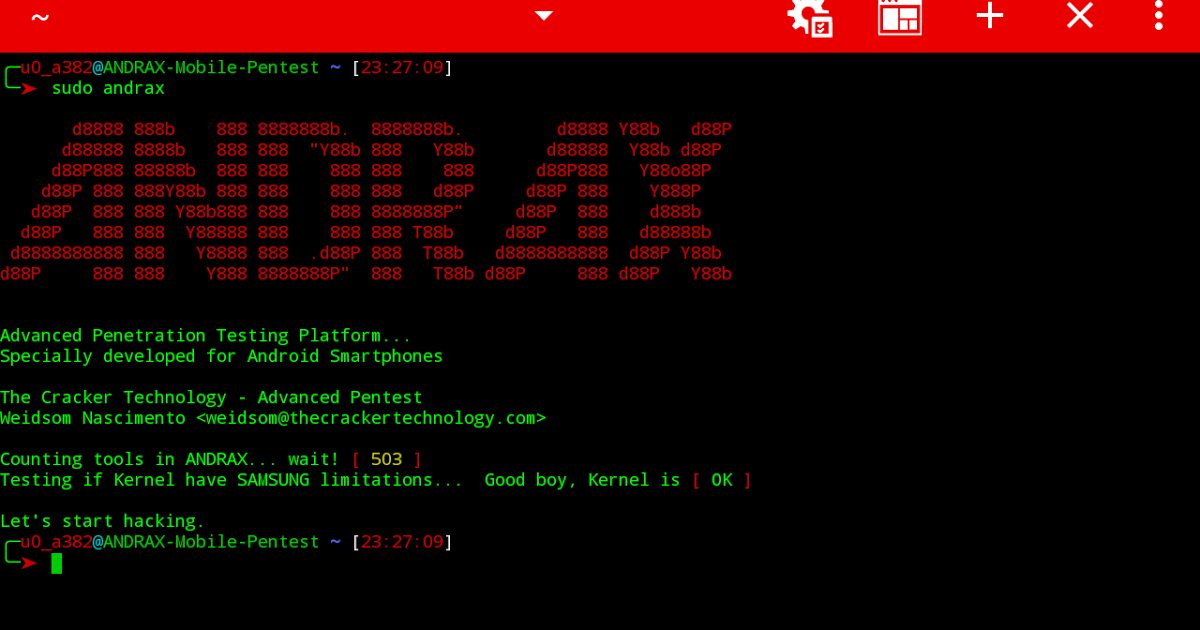
ANDRAX The first and unique Penetration Testing platform for Android smartphones What is ANDRAX ANDRAX is a penetration testing platform developed specifically...
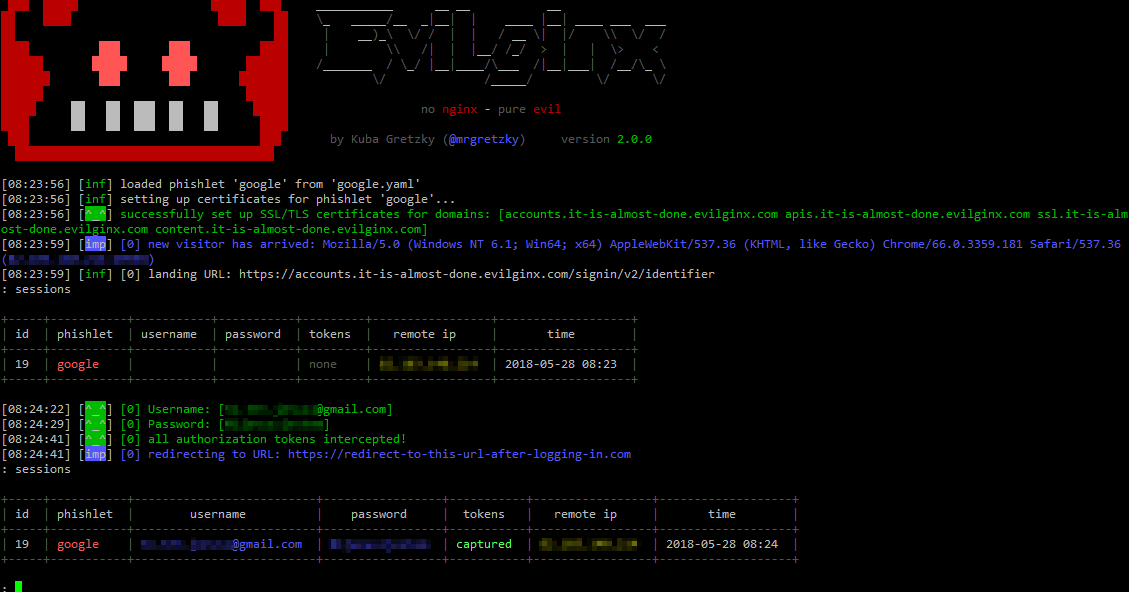
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...