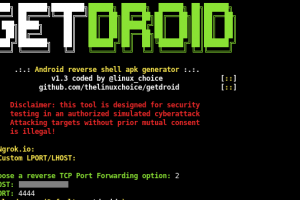
[sc name=”ad_1″] Fully Undetectable Android Payload And Listener Read the license before using any part from this code Malicious Android apk...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
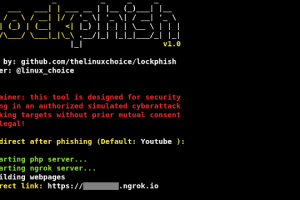
[sc name=”ad_1″] Lockphish it’s the first tool (05/13/2020) for phishing attacks on the lock screen, designed to grab Windows credentials...
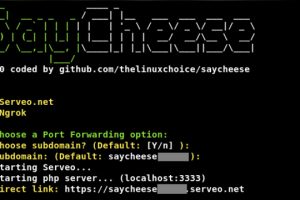
[sc name=”ad_1″] Take webcam shots from target just sending a malicious link. How it works? The tool generates a malicious HTTPS page using Serveo...
[sc name=”ad_1″] Finder Of XSS, and Dal is the Korean pronunciation of moon. What is DalFox Just, XSS Scanning and Parameter Analysis tool. I...
[sc name=”ad_1″] A Undetectable Payload Generation. This tool is for educational purpose only, usage of Kaiten for attacking targets without prior...
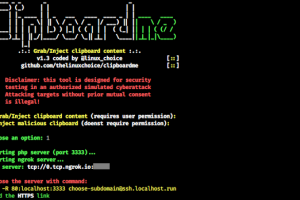
[sc name=”ad_1″] Grab/Inject Clipboard Content Browsers are implementing a new JavaScript API for asynchronous clipboard access to integrate copy...
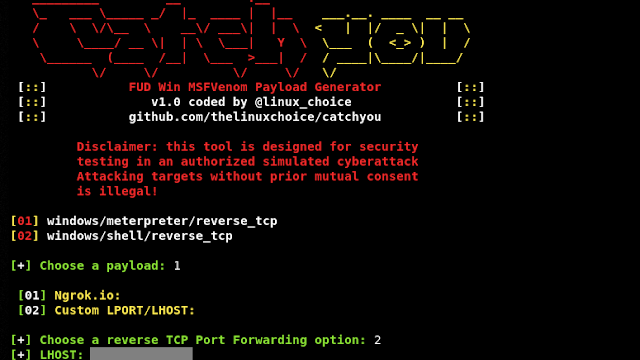
[sc name=”ad_1″] Fully Undetectable Win32 MSFVenom Payload Generator (meterpreter/shell reverse tcp) Author: github.com/thelinuxchoice/catchyou...
[sc name=”ad_1″] A list of useful payloads and bypasses for Web Application Security. Feel free to improve with your payloads and techniques ...
[sc name=”ad_1″] Shellerator is a simple command-line tool aimed to help pentesters quickly generate one-liner reverse/bind shells in multiple...
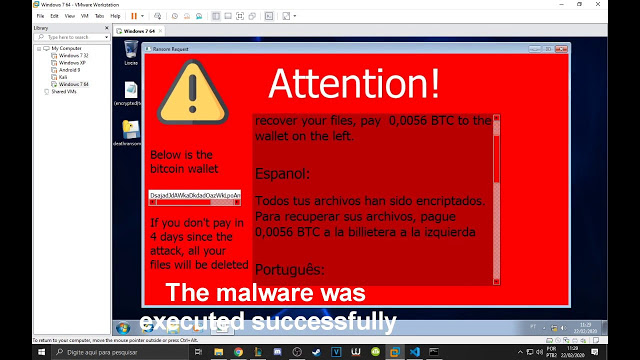
[sc name=”ad_1″] What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a...