[sc name=”ad_1″] A Modular Penetration Testing Framework Install pip install fsociety Update pip install --upgrade fsociety Usage usage: fsociety [...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
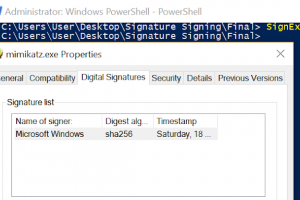
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
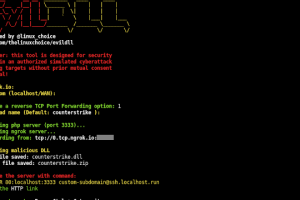
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
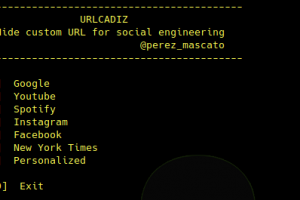
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without...
[sc name=”ad_1″] KeyLogger for Linux Systems. Features Runs on GUI systems or CLI Sending data by email Dependencies curl libx11-dev (Debian-Based)...
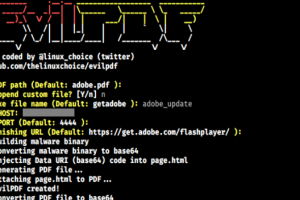
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Hiding executable files in PDF documents Legal disclaimer: Usage of...
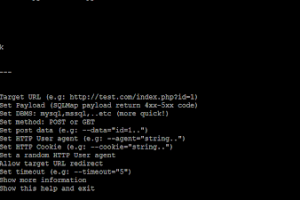
[sc name=”ad_1″] Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code...
[sc name=”ad_1″] This is a basic C2 generic server written in Python and Flask. This code has based ideia to GTRS, which uses Google Translator as...
[sc name=”ad_1″] URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking...
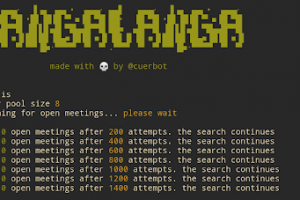
[sc name=”ad_1″] Zoom Conference scanner. This scanner will check for a random meeting id and return information if available. Usage This are all...