The motion seeks to make it more stressful for students to cheat in exams. As a section of the new rules, schools will also be allotted to do history checks on...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
Not the first news of this nature but it was very recently discovered that Microsoft suffered a cyber attack from a group of very intelligent hackers way back...
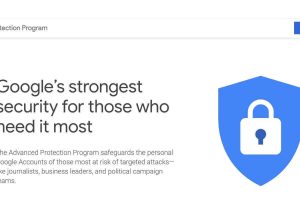
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are...
Studies on the topic of in-browser miners have been going on the Chromium project’s bug tracker since mid-September when Coinhive, the first launched. To...
Agari supports email fraud on behalf of larger than 400 federal websites, including the real sites of the departments of Health and Human Services and Veterans...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
In May 2017, Kaspersky security researchers have noticed a forum post advertising ATM (Automated teller machine) malware that was targeting specific vendor...
Unfortunately, it looks like the method is still in effect. Philip Neustrom, the co-founder of Shotwell Labs, lately found two demo websites that would pass...