A former operations manager existed for Facebook’s privacy works said the company “prioritized data gathering from its users overprotecting them from abuse.”...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
The business allowed 57 people to drive vehicles although they required valid driver’s licenses or had performed other offenses that would have excluded them...
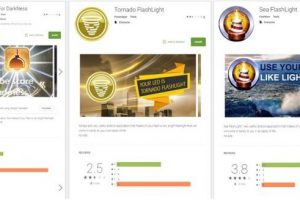
Google made many efforts to make the Play Store away from malicious apps, but some apps were able to fool the anti-malware protections and infect users with...
It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
The firm looked at nearly 70 million emails sent during October from 5,000 different .gov origin domains preserved by Proofpoint, the company’s VP of Email...
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
Another crop of Android apps hiding malware have been discovered in – and removed from – the Google Play store. Researchers at ESET discovered...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...