This scam email is nearly well designed. The scammers are using a template system to create individualized reports with specific recipient data. This works...
Author - Mazen Elzanaty
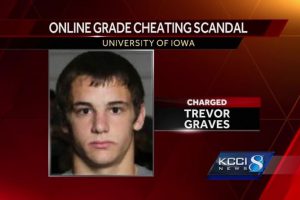
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...
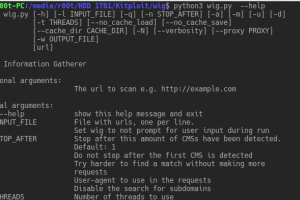
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
A robust Phishing Framework with a full featured CLI interface. The project was born out necessity through of years of engagements with tools that just didn’t...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
A Facebook post promoting rape videos was also allowed to stay online despite being informed several times, the court listened, while police in the western...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
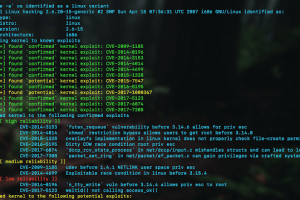
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...