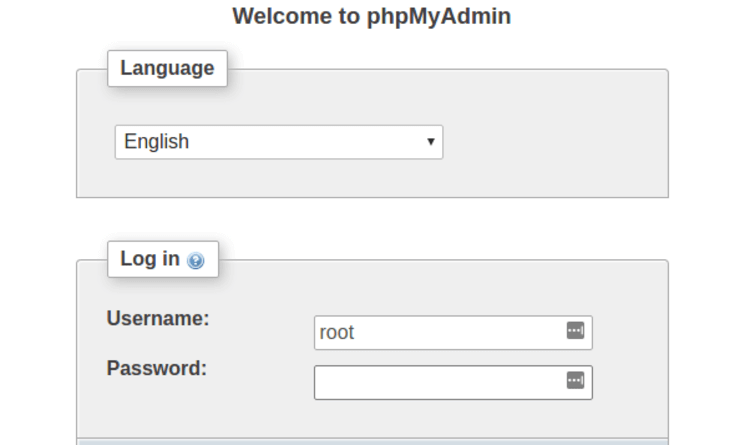
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
Author - Mazen Elzanaty
The streaming company retweeted its care for the Internet Association’s Friday announced it would “interrupt in a judicial action to save net neutrality...
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
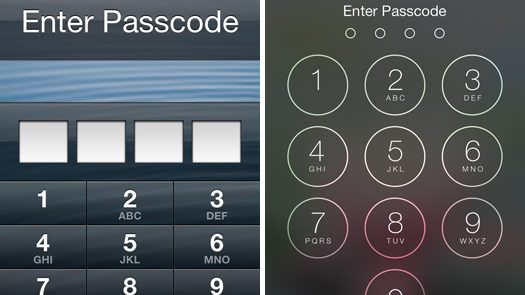
This version of the application is written with Python programming language,which is used to crack the Restriction PassCode of iphone/ipad. Brute Force Get the...
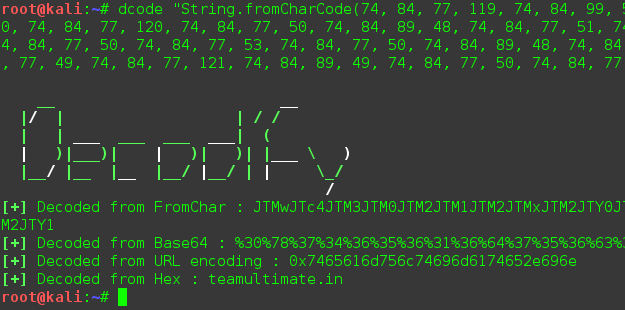
Decodify can detect and decode encoded strings, recursively. Its currently in beta phase. Lets take this string : teamultimate.in and encode it with Hex, URL...
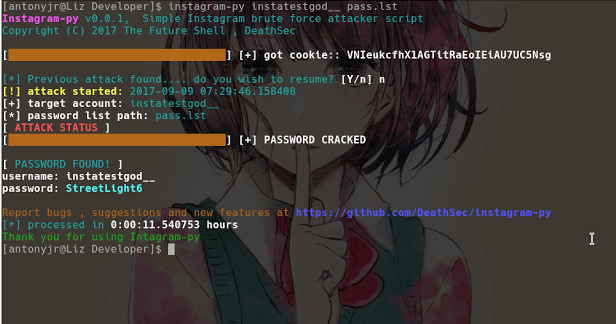
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
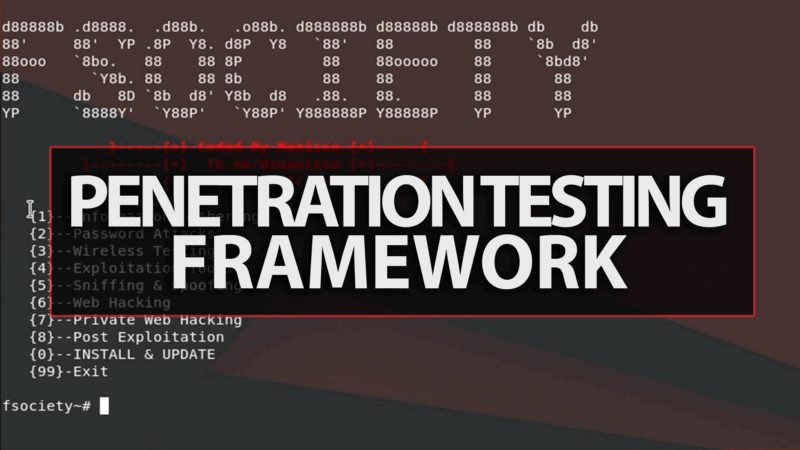
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
In today’s world, no company is fully safe as even big names like Sony and HBO have been hacked, and quite recently Nintendo’s Switch had to go through the...
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...