[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
Author - Mazen Elzanaty
[sc name=”ad_1″] A (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which...
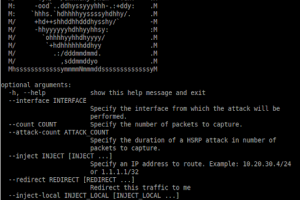
[sc name=”ad_1″] Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic...
[sc name=”ad_1″] Invoke-AntiVM is a set of modules to perform VM detection and fingerprinting (with exfiltration) via Powershell. Compatibility Run...
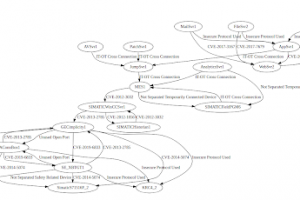
[sc name=”ad_1″] An organizational asset and vulnerability management tool, with Jira integration, designed for generating application security...
[sc name=”ad_1″] Tool to manipulate and insert tracking pixels into Office Open XML documents. Features Insert tracking pixels into Office Open XML...
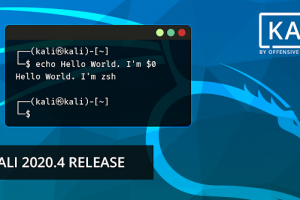
[sc name=”ad_1″] Time for another Kali Linux release! – Kali Linux 2020.4. This release has various impressive updates: ZSH is the new default...
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
[sc name=”ad_1″] Ping, but with a graph. Install FYI: The old Python version can be found under the python tag. Homebrew (MacOS + Linux) brew tap...