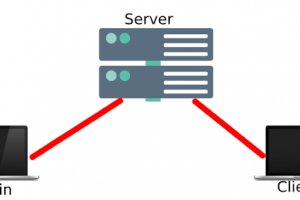
[sc name=”ad_1″] How it works? 1- Build server 2- Connect with admin and client to server 3- To collect information, send the request to the server...
Archive - October 2020
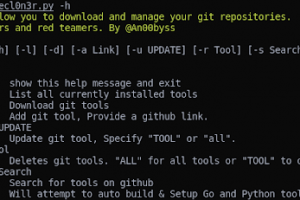
[sc name=”ad_1″] TheCl0n3r will allow you to download and manage your git repositories. Preface About 90% of the penetration testing tools used in...
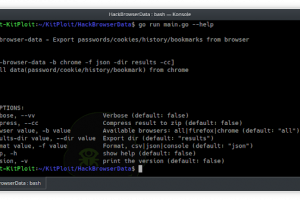
[sc name=”ad_1″] hack-browser-data is an open-source tool that could help you decrypt data (passwords / bookmarks / cookies / history) from the...
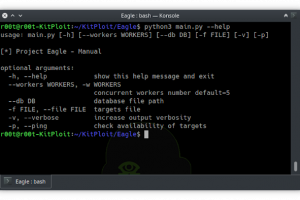
[sc name=”ad_1″] Project Eagle is a plugin based vulnerabilities scanner with threading support used for detection of low-hanging bugs on mass...
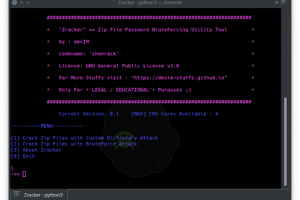
[sc name=”ad_1″] Zracker is a Zip File Password BruteForcing Utility Tool based on CPU-Power. Yet available for Linux only … Supports...
[sc name=”ad_1″] Mail Swipe is a python script that helps you to create temporary email addresses and receive emails at that address. It uses the...
[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
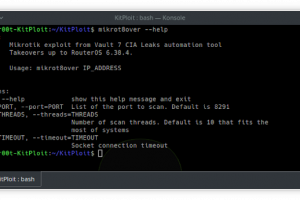
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
[sc name=”ad_1″] Nuubi Tools: Information-ghatering|Scanner|Recon Options: -h/--help | Show help message and exit Arguments: -b/--banner | Banner...
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...