[sc name=”ad_1″] Most of us are very curious to know a method to send spoofed emails to our friends and family for fun. But the question is, is it...
Archive - May 2018
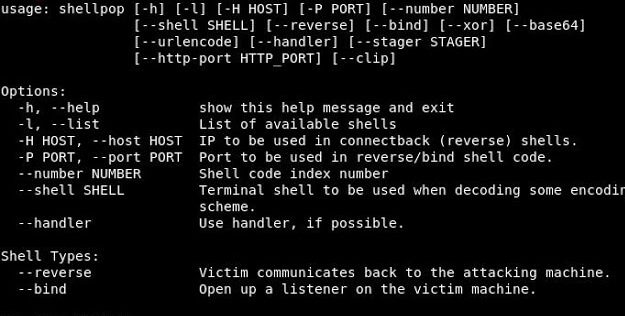
Pop shells like a master Shell pop is all about popping shells. With this tool you can generate easy and sofisticated reverse or bind shell commands to help...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
Author: Cole Gibson Before it became intertwined in the controversy surrounding Facebook’s misuse of data, Cambridge Analytica was planning to raise funds for...
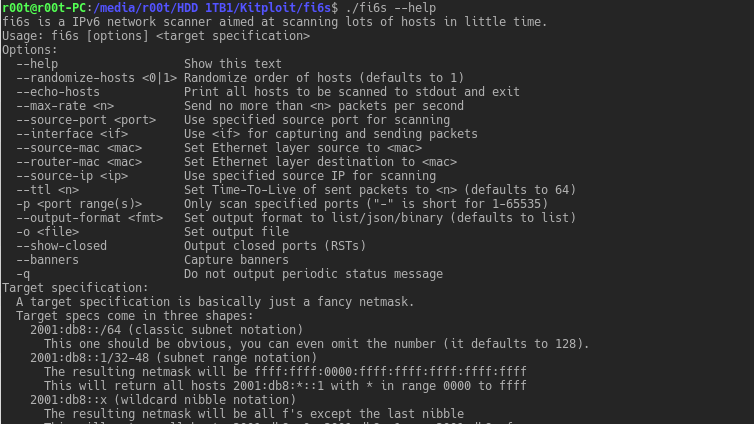
fi6s is a IPv6 port scanner designed to be fast. This is achieved by sending and processing raw packets asynchronously. The design and goal is pretty similar...
This Kali release is the first to include the Linux 4.15 kernel, which includes the x86 and x64 fixes for the much-hyped Spectre and Meltdown vulnerabilities...
The single most common causes of a broken Kali Linux installation are following unofficial advice, and particularly arbitrarily populating the system’s sources...