[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...
Archive - April 2018
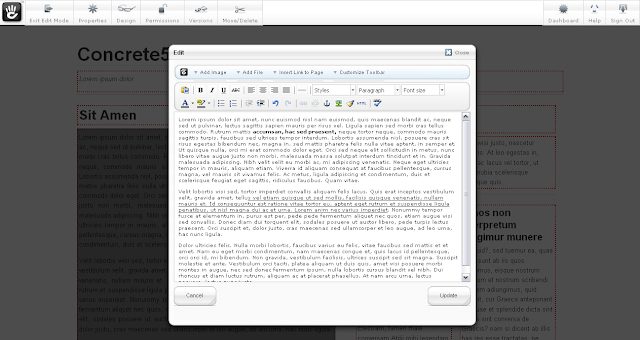
Vulnerability scanner and information gatherer for the Concrete5 CMS. Is a little out of date presently pending a refactor. concrete5 is an open-source content...
This will be the beggining of a long series of the basics of linux, so let’s get started. What is Linux? Open-Source? What is the use of Linux? Linux is...
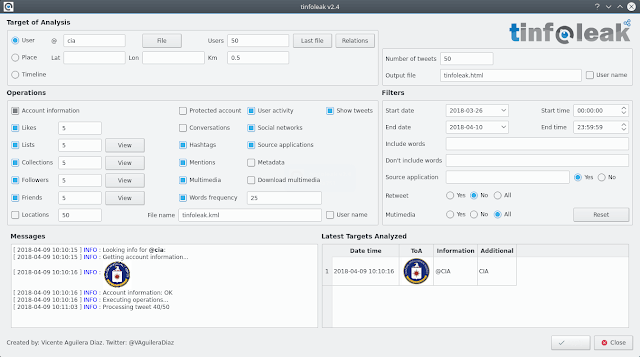
The most complete open-source tool for Twitter intelligence analysis Introduction tinfoleak is an open-source tool within the OSINT (Open Source Intelligence)...
CloudFrunt is a tool for identifying misconfigured CloudFront domains. CloudFront is a Content Delivery Network (CDN) provided by Amazon Web Services (AWS)...
Sandmap is a tool supporting network and system reconnaissance using the massive Nmap engine. It provides a user-friendly interface, automates and speeds up...
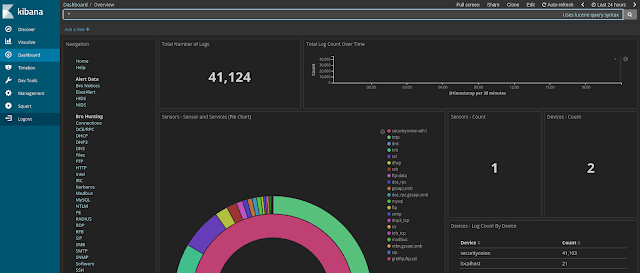
Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes...
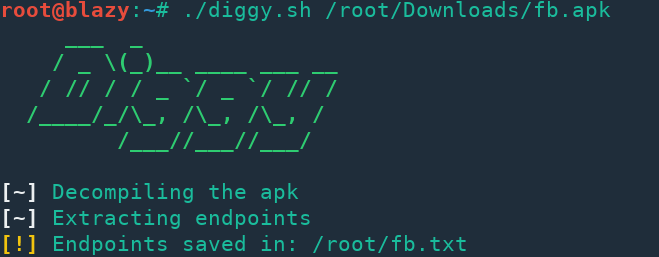
Diggy can extract endpoints/URLs from apk files. It saves the result into a txt file for further processing. Dependencies apktool Usage ./diggy.sh...
Author: Colin Harper If you’ve ever dealt in Bitcoin, you may have suffered through hour-long (or at worst, day-long) transaction times. It’s becoming...
CHAOS allow generate payloads and control remote Windows systems. Features Reverse Shell Download File Upload File Screenshot ? Keylogger ? Persistence Open...