TopHat is inspired by metasploit’s capabilties of meterpreter however it was coded to generate a undetected encrypted backdoor using python. Usage:...
Archive - February 2018
Author: Erin Gorsline The move marks the first time a Japanese Bank will launch a cryptocurrency and exchange. Worth more than financial mega-giant Bank of...
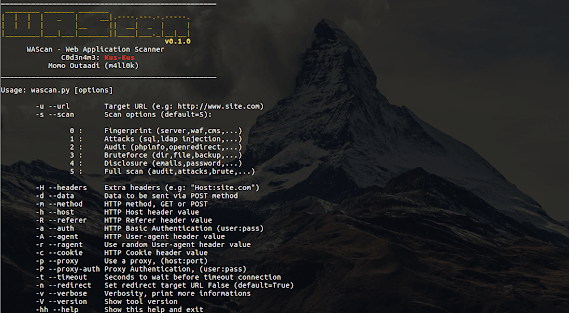
WAScan ((W)eb (A)pplication (Scan)ner) is a Open Source web application security scanner. It is designed to find various vulnerabilities using “black...
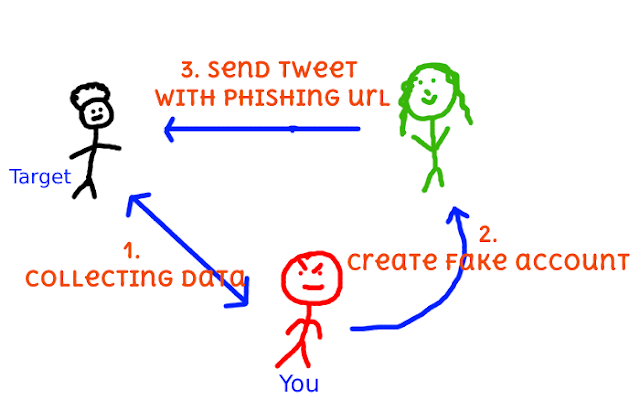
How it works? 1- Collect data from target’s twitter account 2- Find target’s friend and copy her/him account 3- Generate tweet automatically with...
mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing. It can be used to intercept, inspect, modify and...
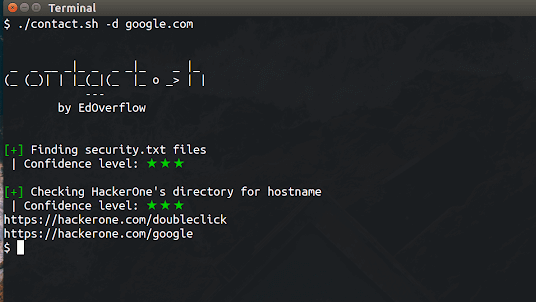
An OSINT tool to find contacts in order to report security vulnerabilities. Installation Linux Make sure you have installed the whois and jq packages. $ git...
MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...
MSDAT (Microsoft SQL Database Attacking Tool) is an open source penetration testing tool that tests the security of Microsoft SQL Databases remotely. Usage...
GlobaLeaks is an open-source, free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...