ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
Archive - December 2017
“This is the start of a long legal battle. Netflix stands w/ innovators, large & small, to oppose this confused FCC order,” the company tweeted quickly...
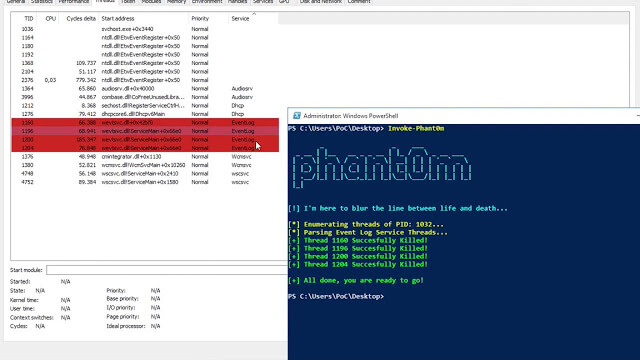
This script walks thread stacks of Event Log Service process (spesific svchost.exe) and identify Event Log Threads to kill Event Log Service Threads. So the...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...
As per many security reports, managements systems of buildings all over the world have improved dramatically, however, their security is still at a large risk...
Security researchers from FireEye and Dragos have discovered a nasty piece of malware targeting industrial control systems (ICS). The malware (called “TRITON”...
A new plug-in called “Looking Glass” discovered in each instance of the new Firefox Quantum browser. It was turned off by default, but users were still scared...
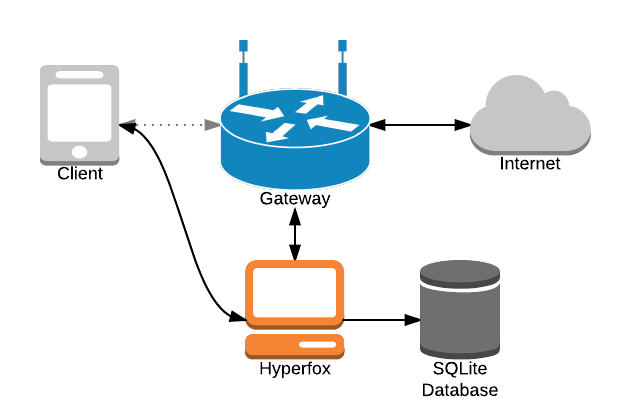
Hyperfox is a security tool for proxying and recording HTTP and HTTPs communications on a LAN. Hyperfox is capable of forging SSL certificates on the fly if...
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
dirsearch is a simple command line tool designed to brute force directories and files in websites. Operating Systems supported Windows XP/7/8/10 GNU/Linux...