BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard...
Archive - December 2017
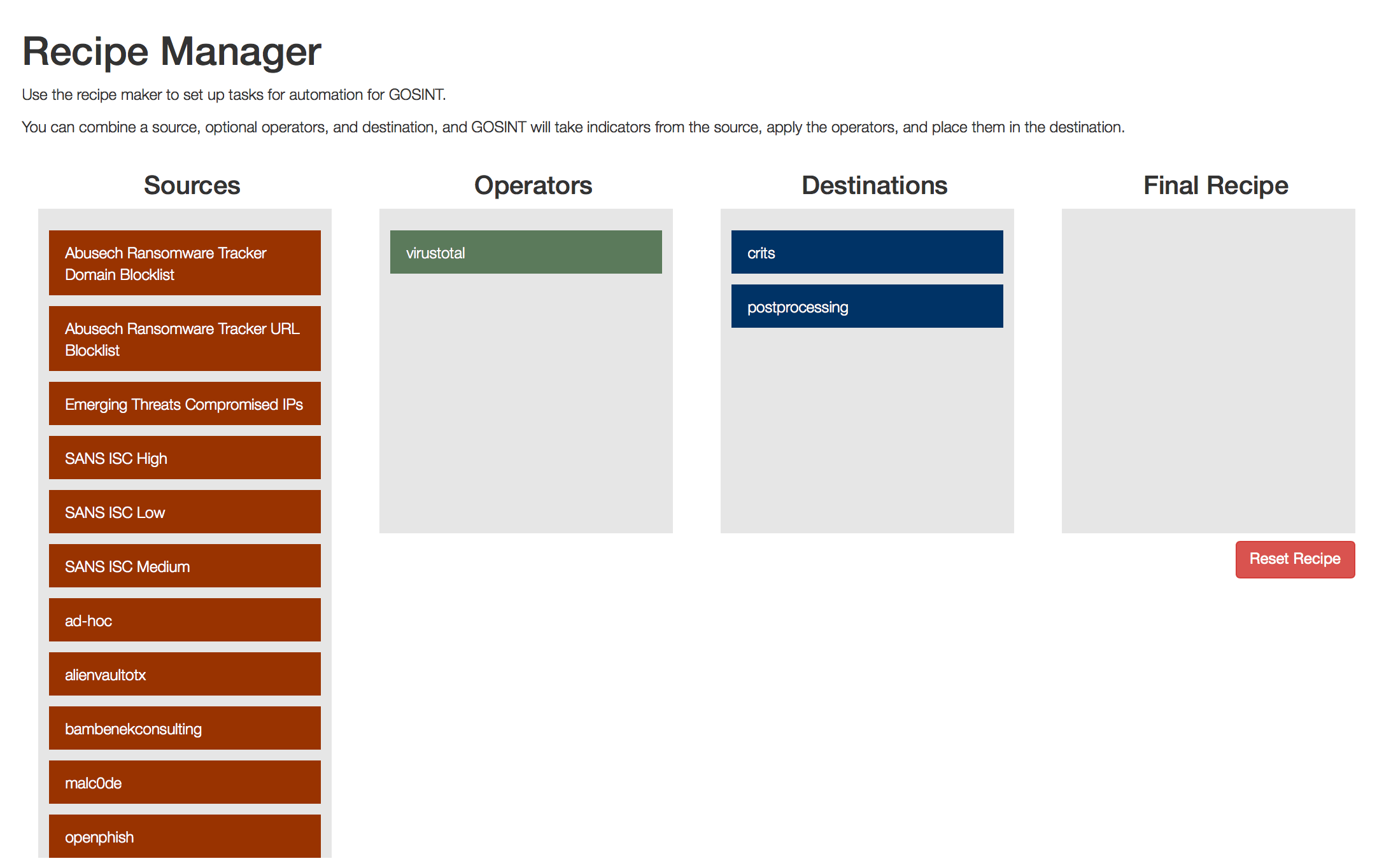
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...
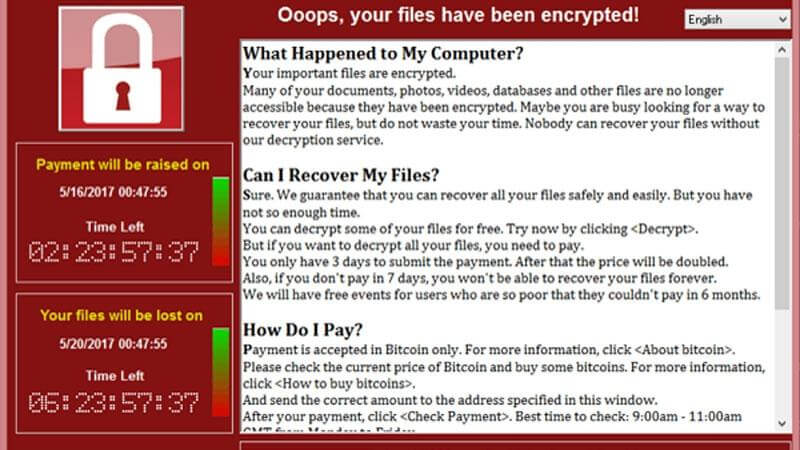
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK...
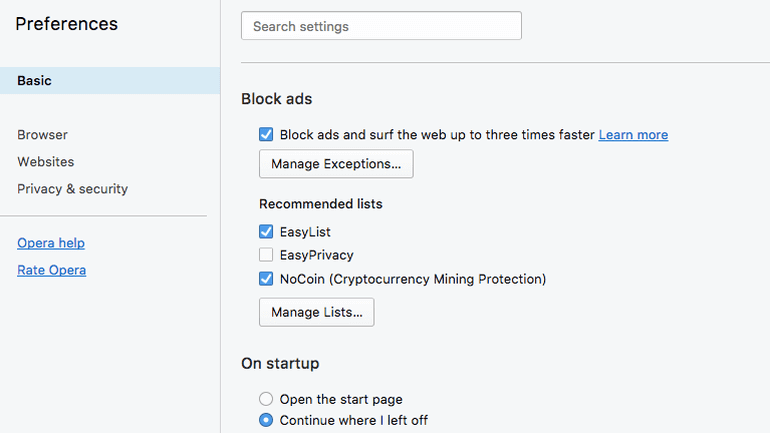
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
In a statement on Wednesday, the organization said slowing down the telephones via a recent software update was needed because the aging batteries in older...
Youbit is a South Korean exchange that got hacked last week. As per reports, it is believed that around one-fifth of the clients’ holdings were stolen by...
Security researchers from security firm Elttam have discovered a critical vulnerability (tracked as CVE-2017-17562) in GoAhead tiny web server that affects...
Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are...