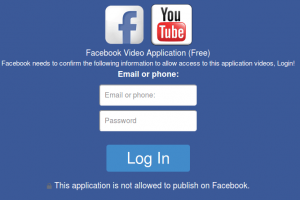
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
Archive - October 2017
SpaceX has begun, on average, about 1.5 times per period during this year. From that view, the company’s 16th launch of 2017 may not appear all that...
FireEye’s Innovation and Custom Engineering (ICE) team released a tool called GoCrack that allows red teams to efficiently manage password cracking tasks...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Are you a proud iPhone owner? If yes, this could freak you up. Trust me! Your iPhone has a serious privacy concern that allows iOS app developers to take your...
Use nmap to scan hidden “onion” services on the Tor network. Minimal image based on alpine, using proxychains to wrap nmap. Tor and dnsmasq are run as daemons...
Canvas fingerprinting relies on websites meaning able to receive data from HTML canvas details calmly. In future, Firefox users will be required to give their...
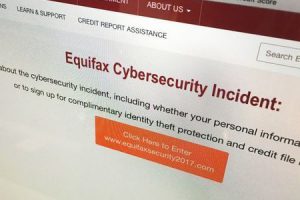
“I don’t remember if my data has been sold to the dark web or where this goes,” she said. “I keep getting letters from Kohl’s, from Macy’s, from Old Navy...