[sc name=”ad_1″] Karkinos is a light-weight ‘Swiss Army Knife’ for penetration testing and/or hacking CTF’s. Currently, Karkinos...
Search Results For - /Configuration
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
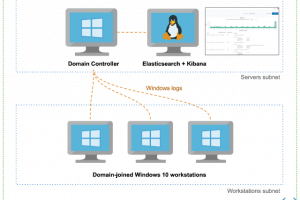
[sc name=”ad_1″] This project allows you to easily spin up Active Directory labs in Azure with domain-joined workstations, Windows Event...
[sc name=”ad_1″] Hardened Debian GNU/Linux and CentOS 8 distro auditing. The main test environment is in debian GNU/Linux 9/10 and CentOS 8, and...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
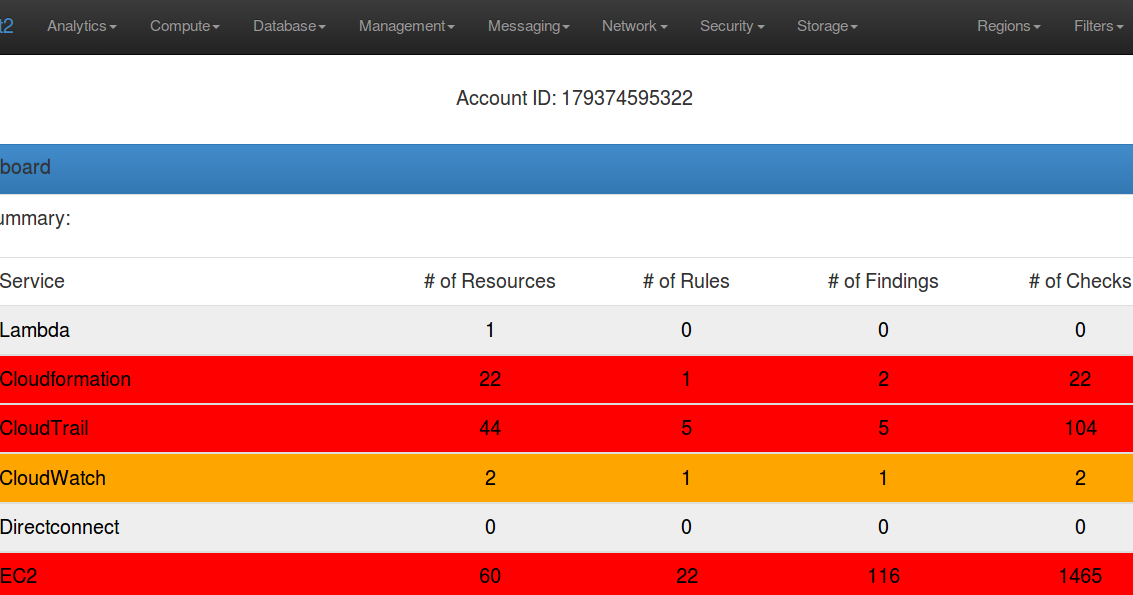
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
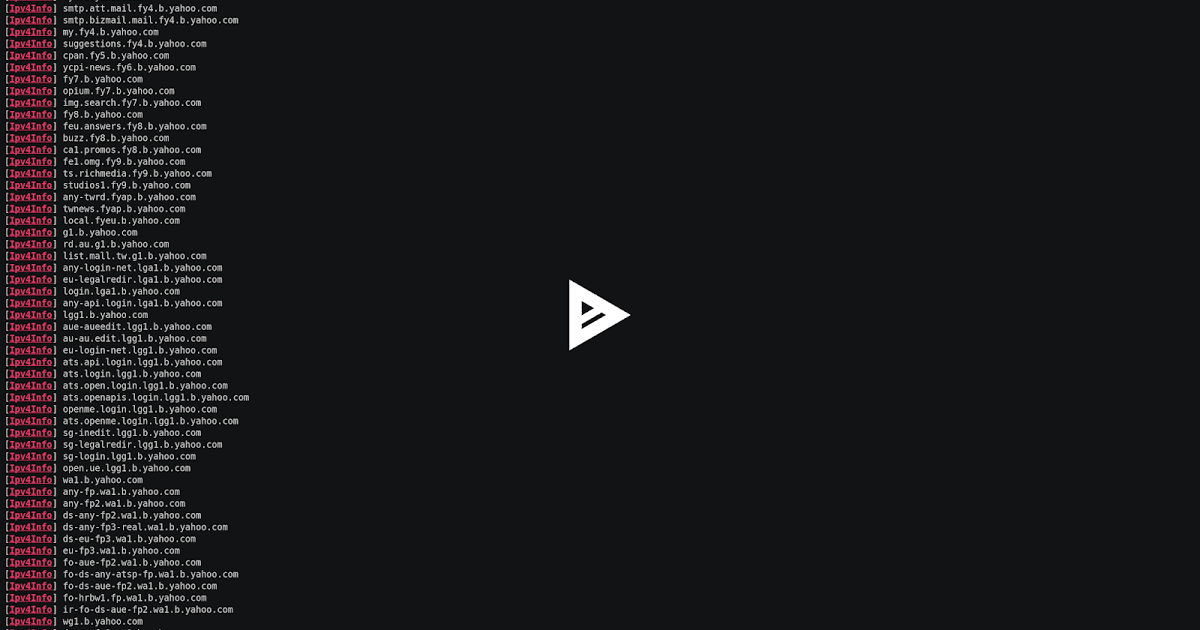
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
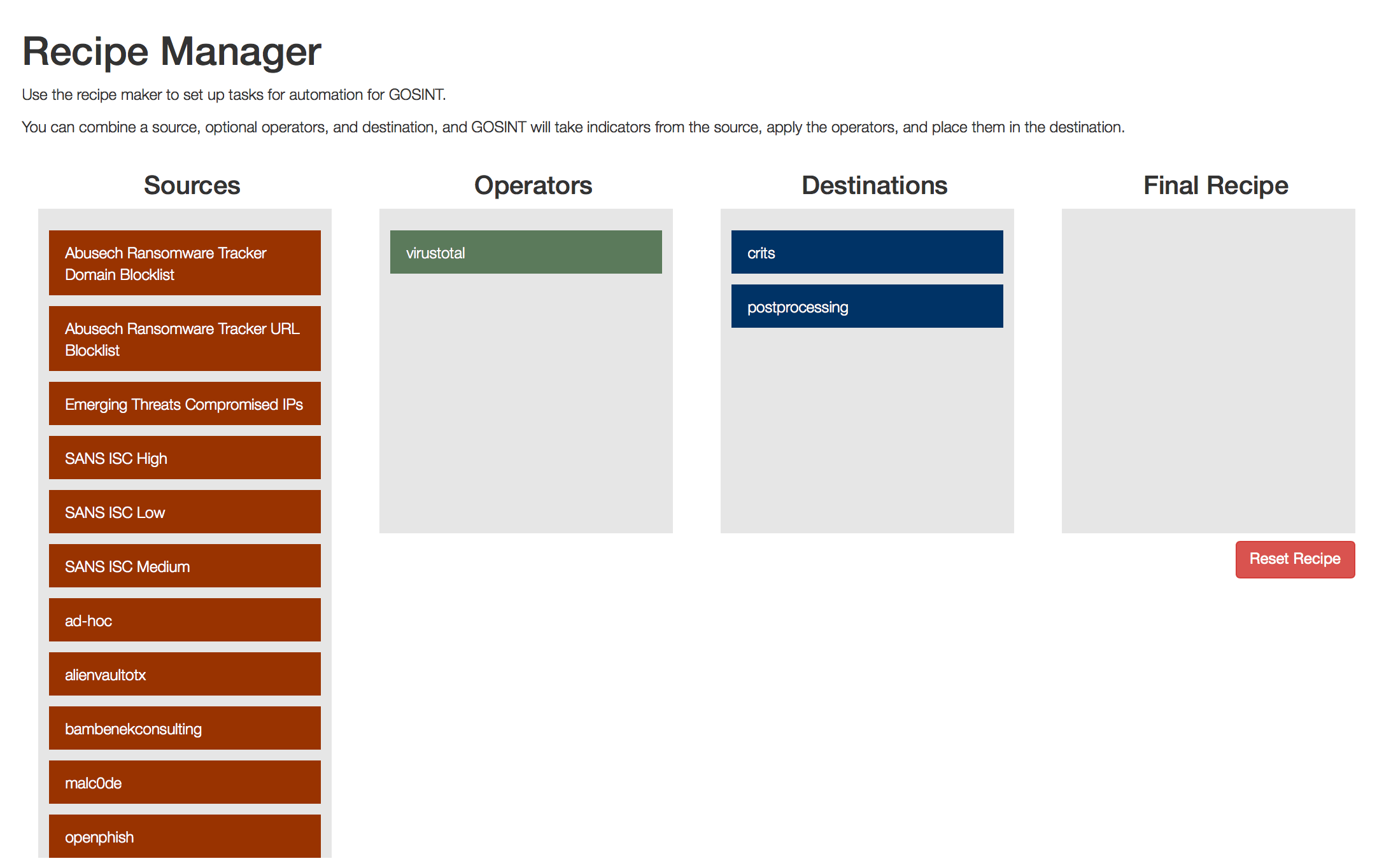
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...